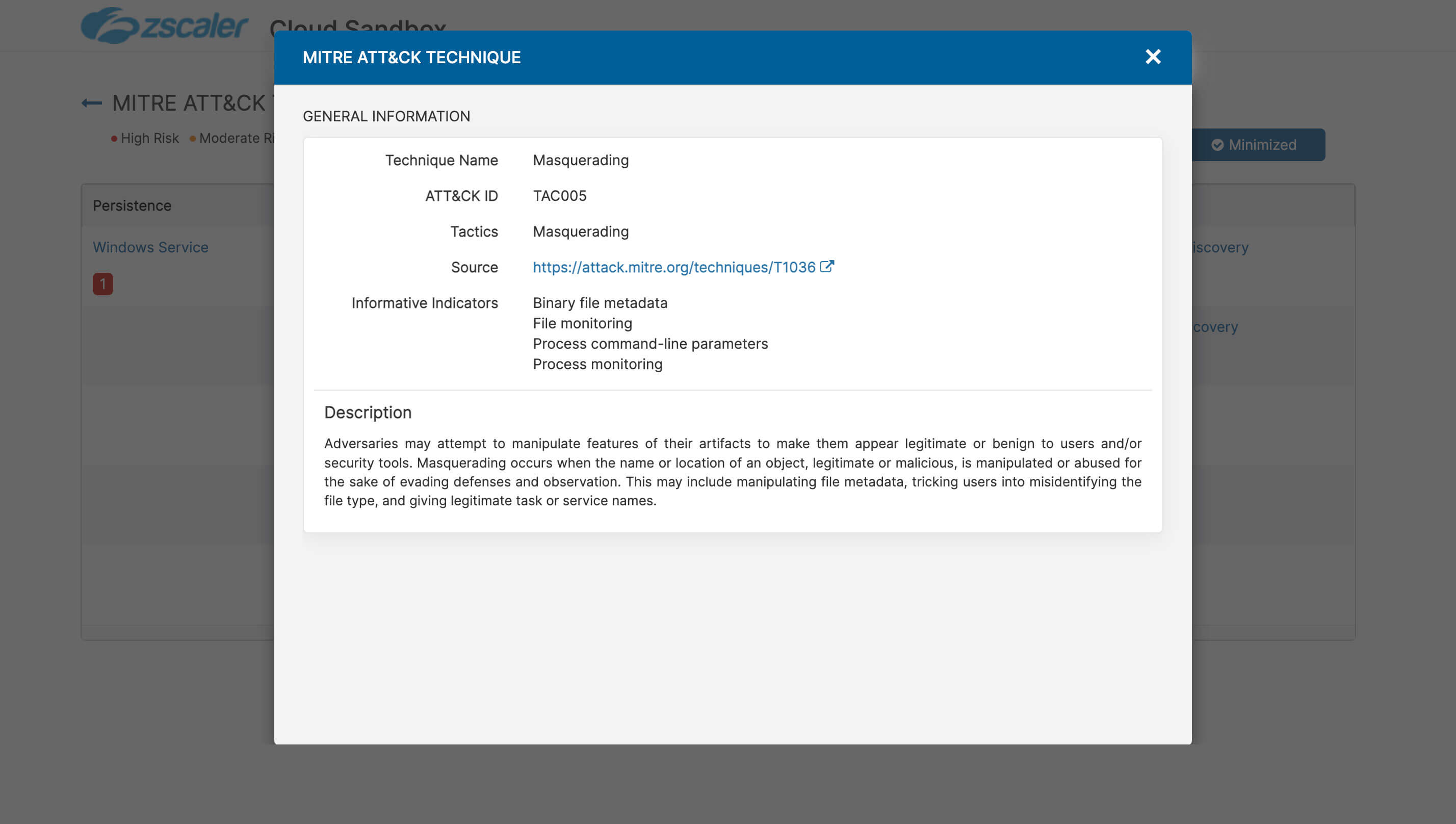
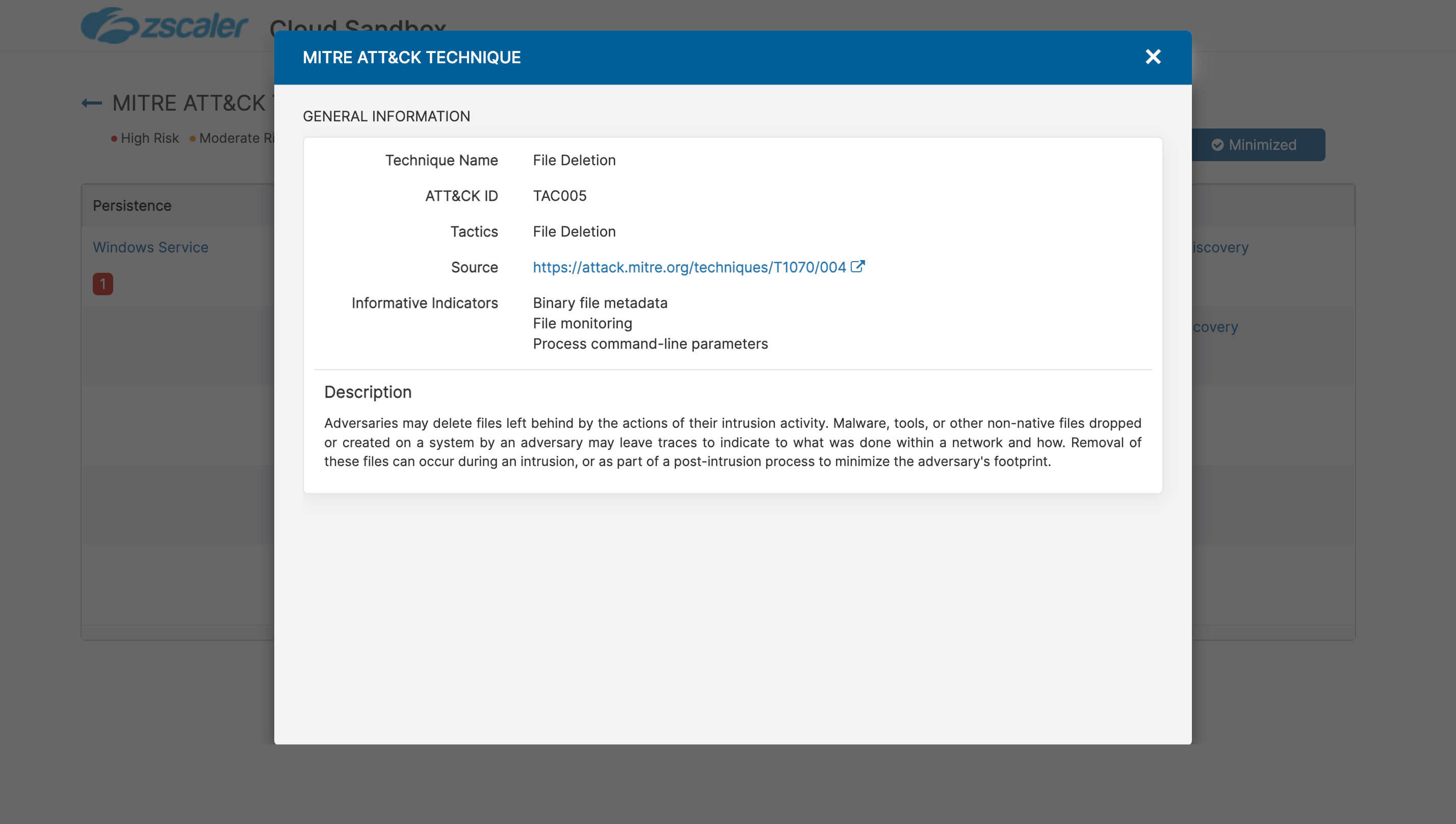
Hope you
enjoyed the tour!
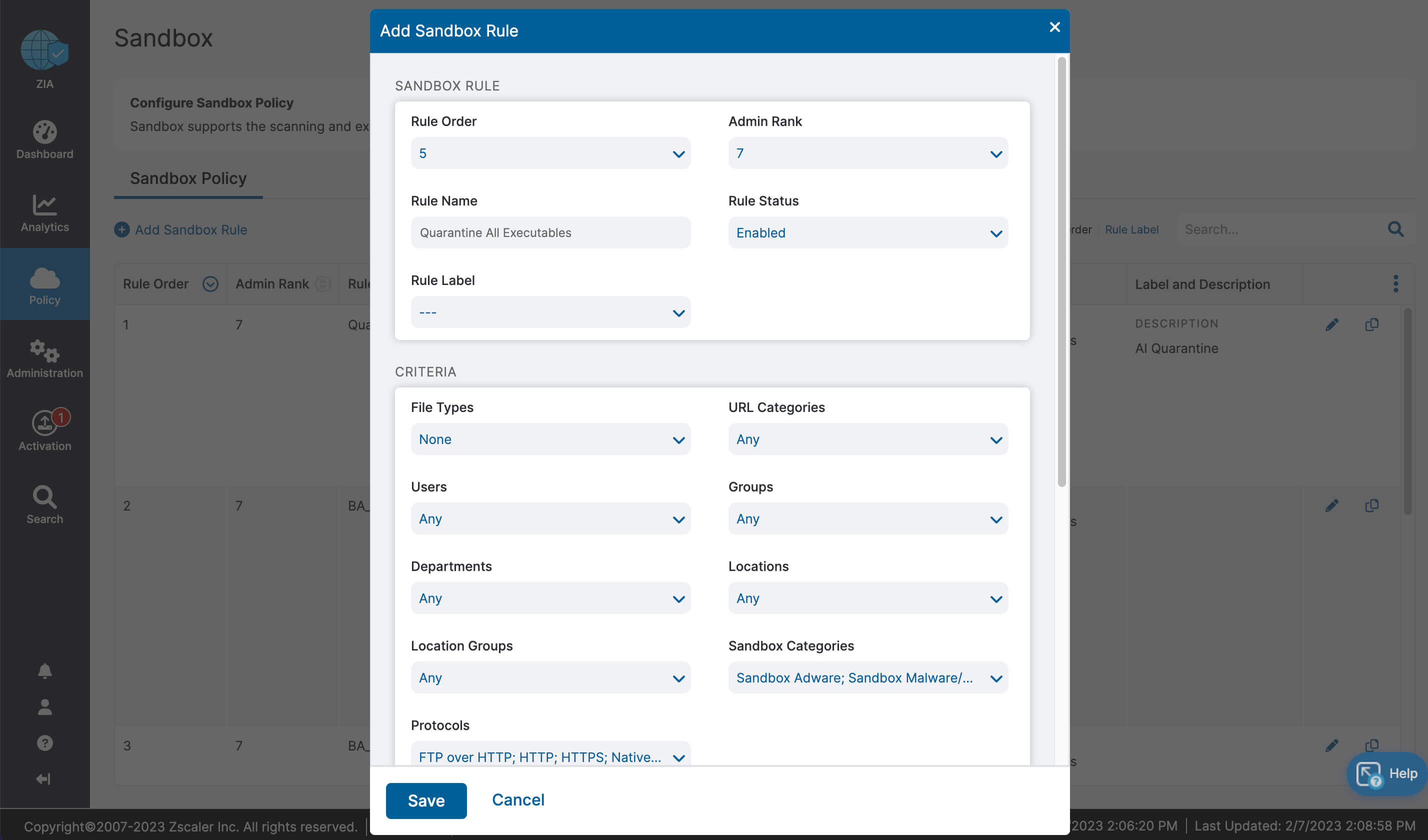
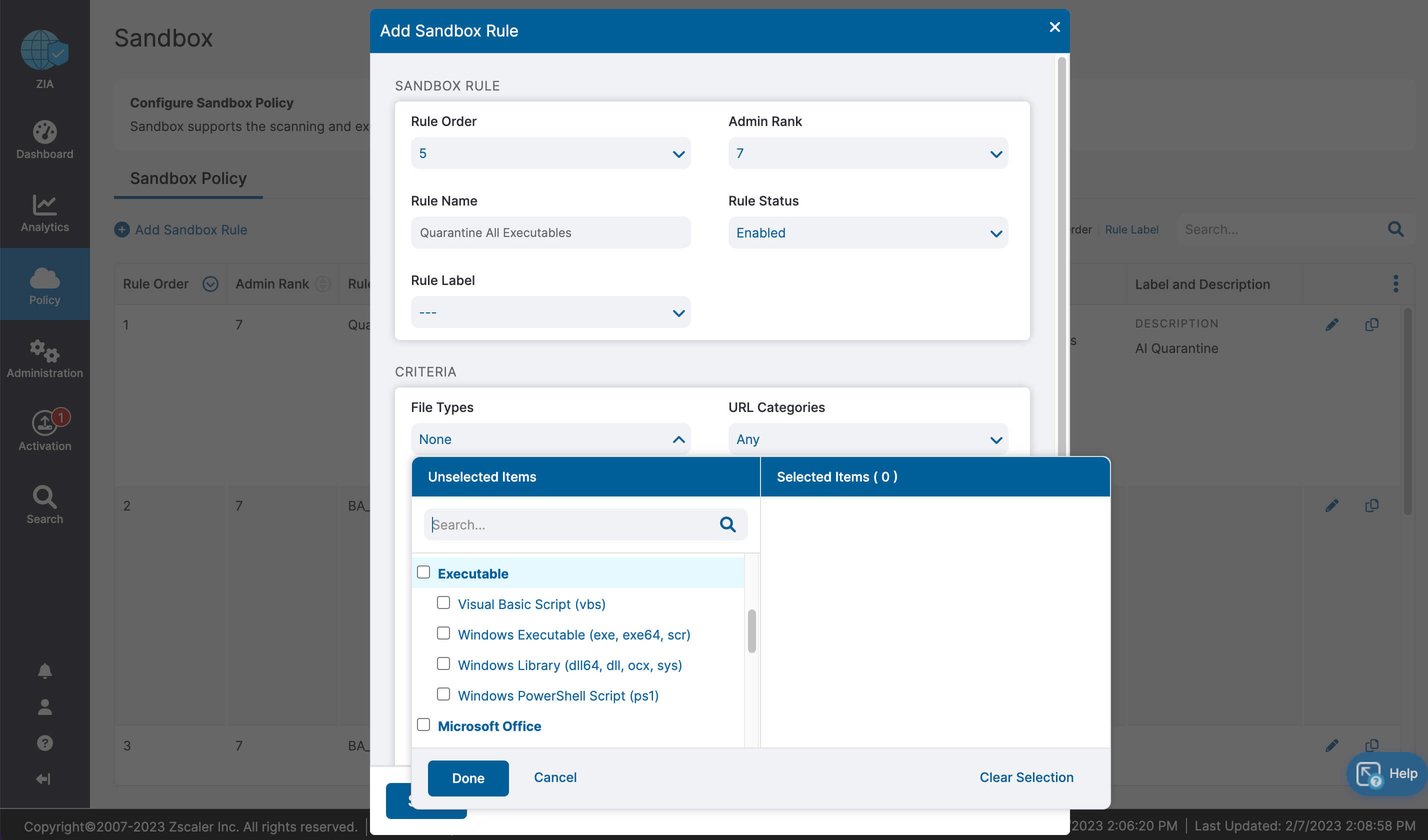
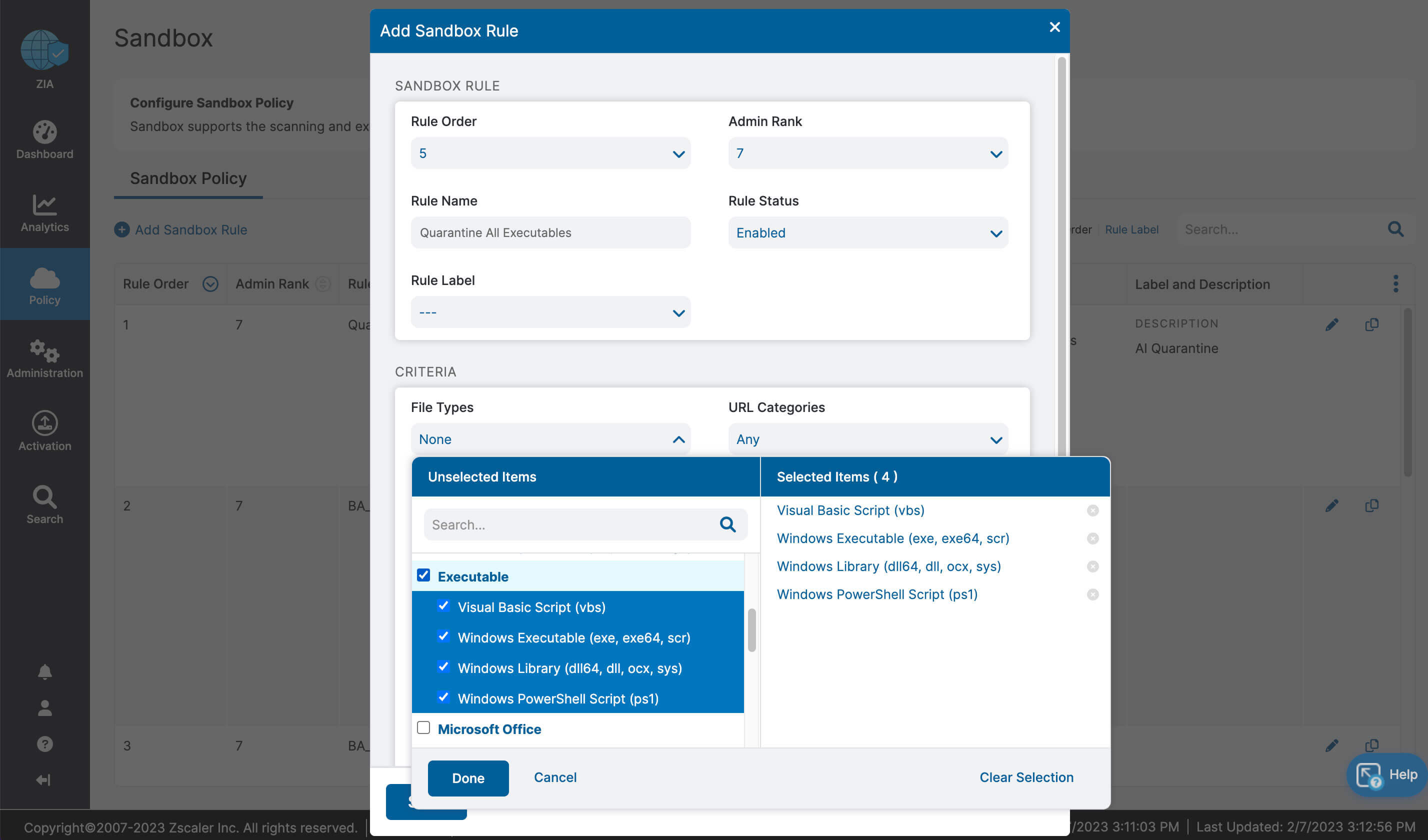
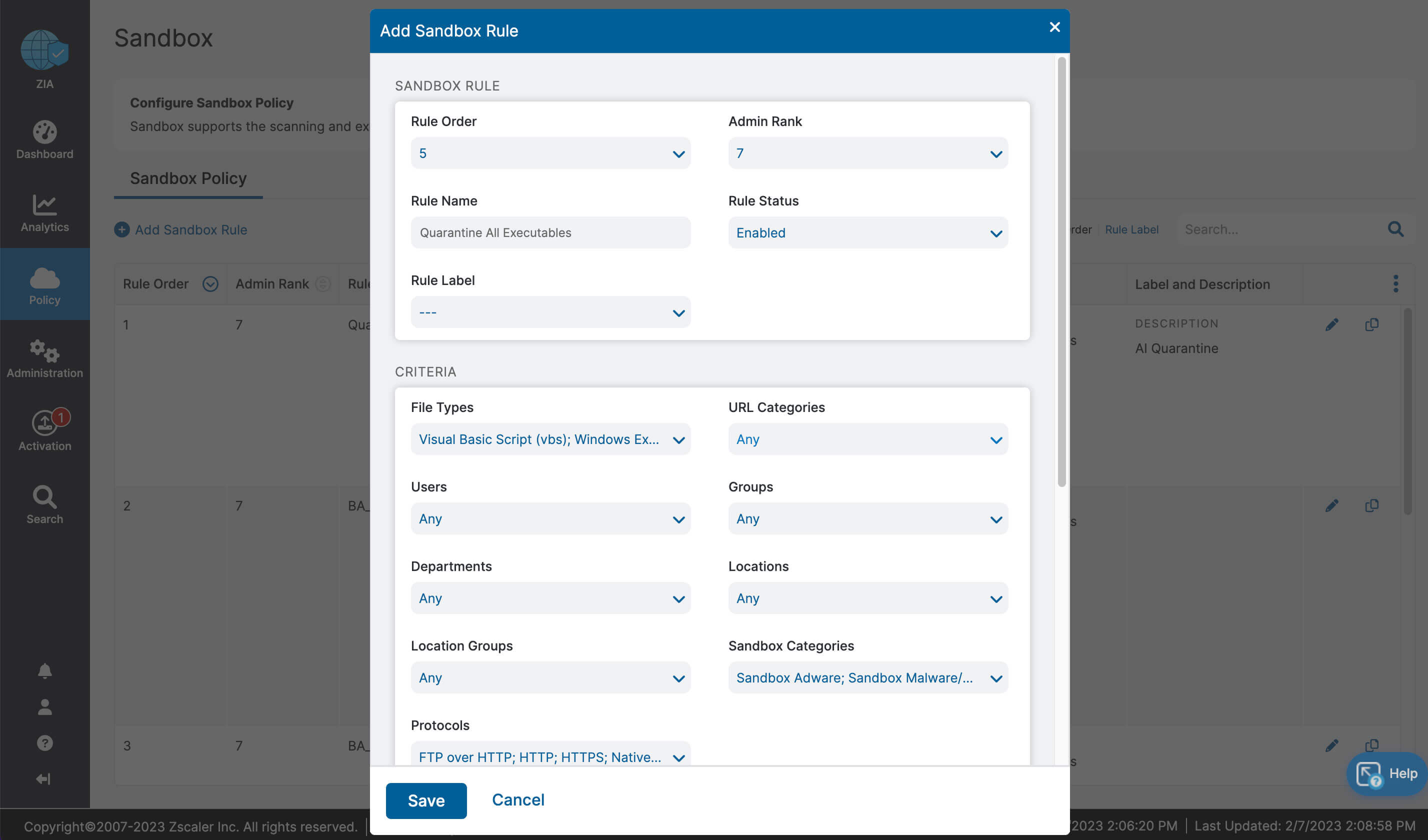
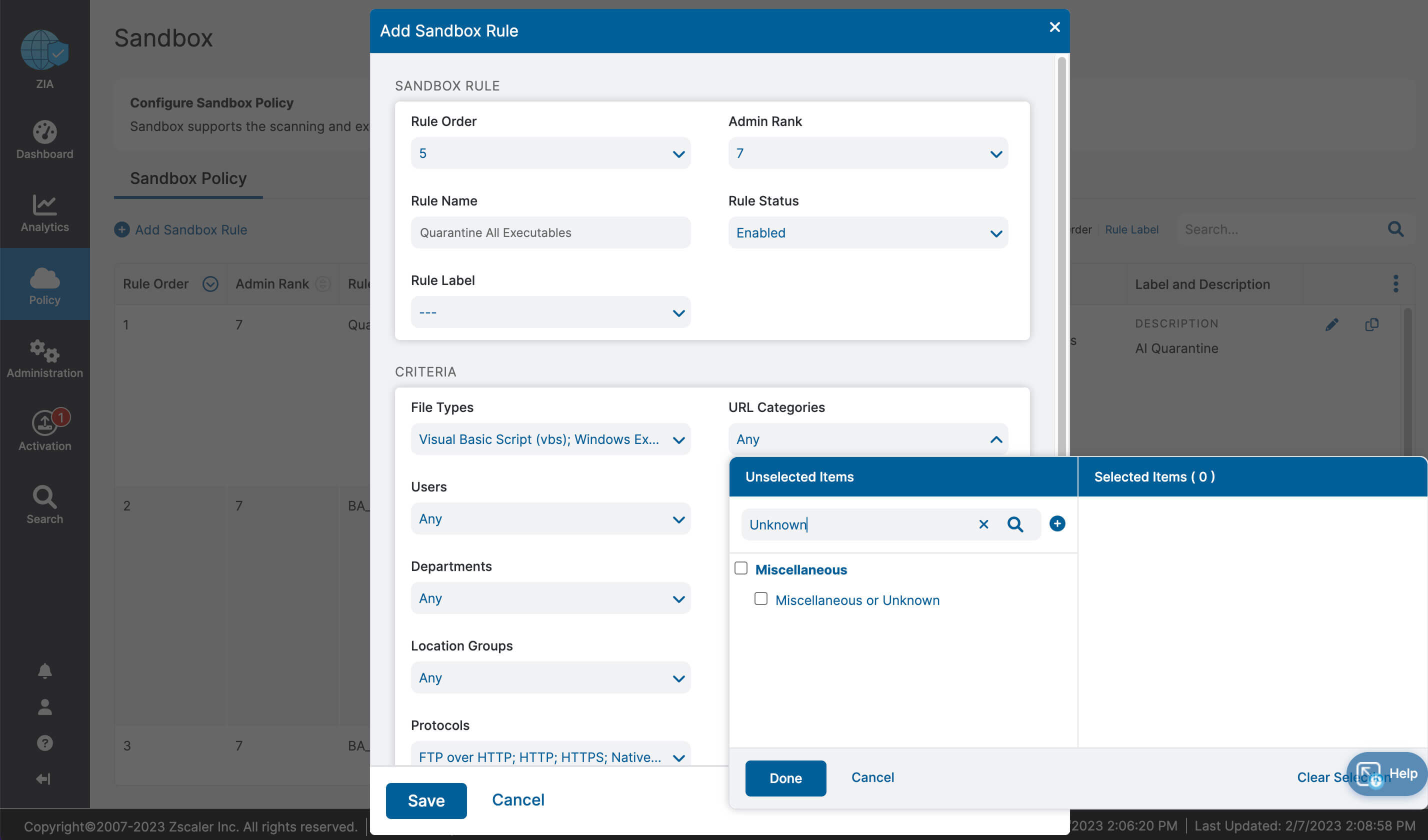
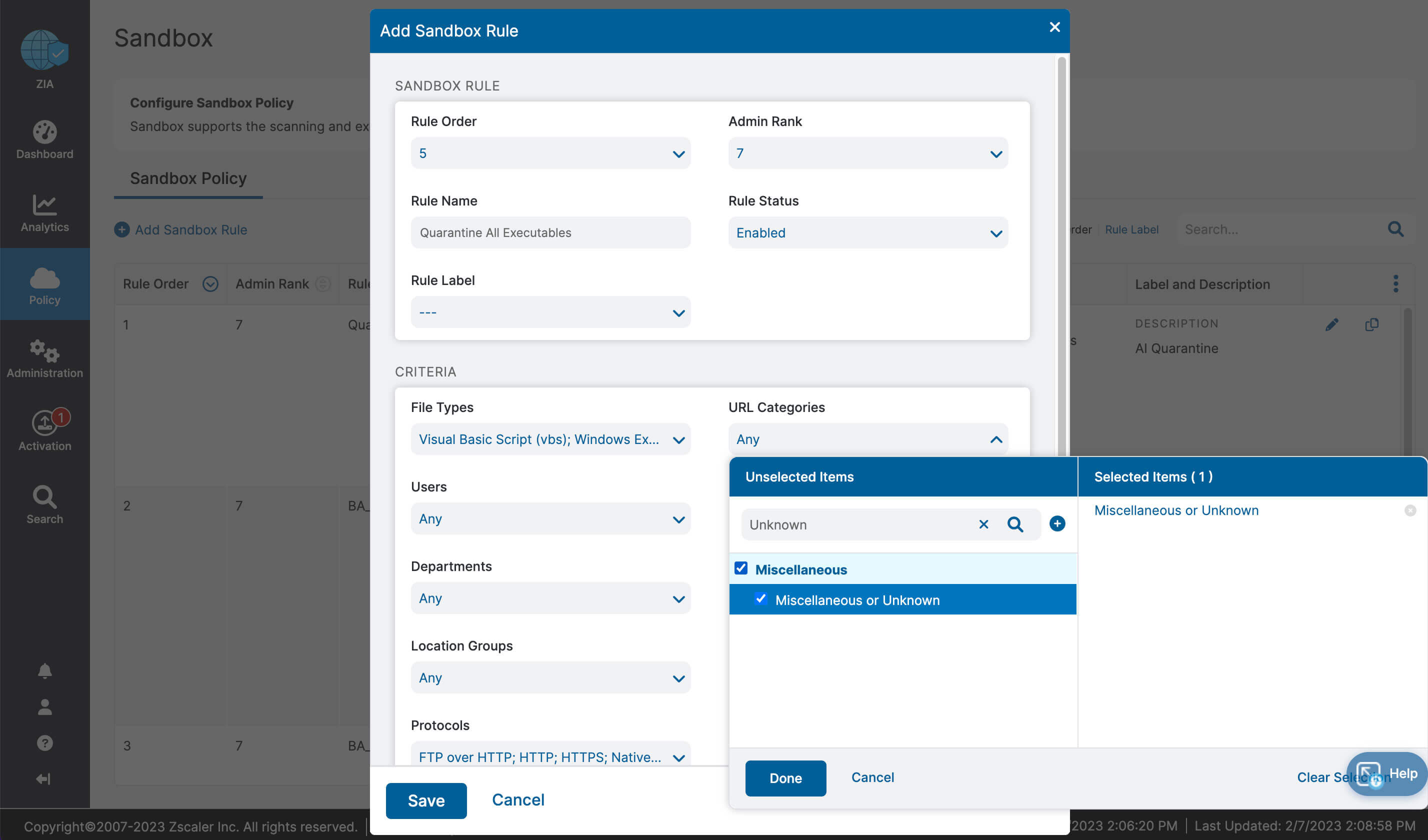
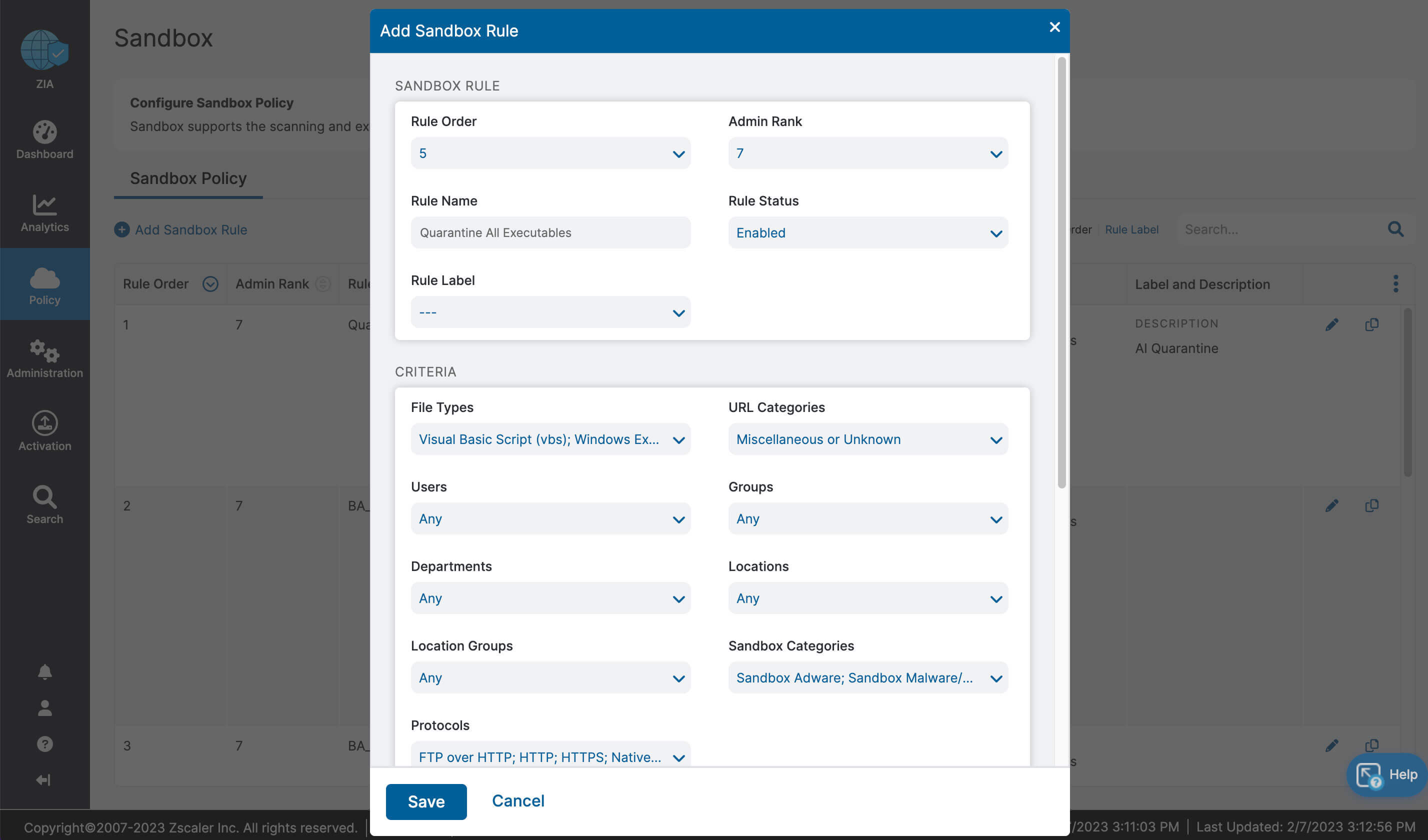
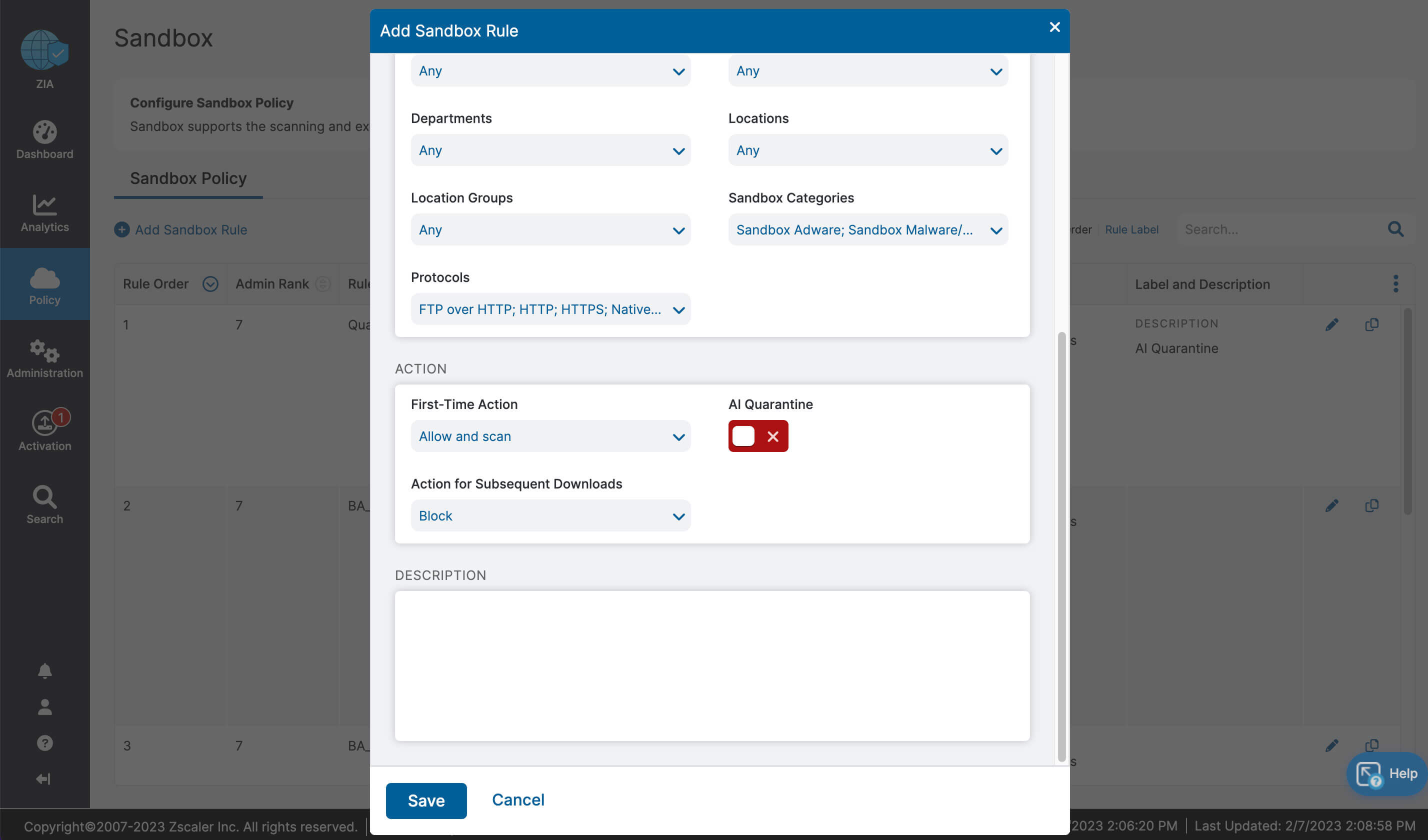
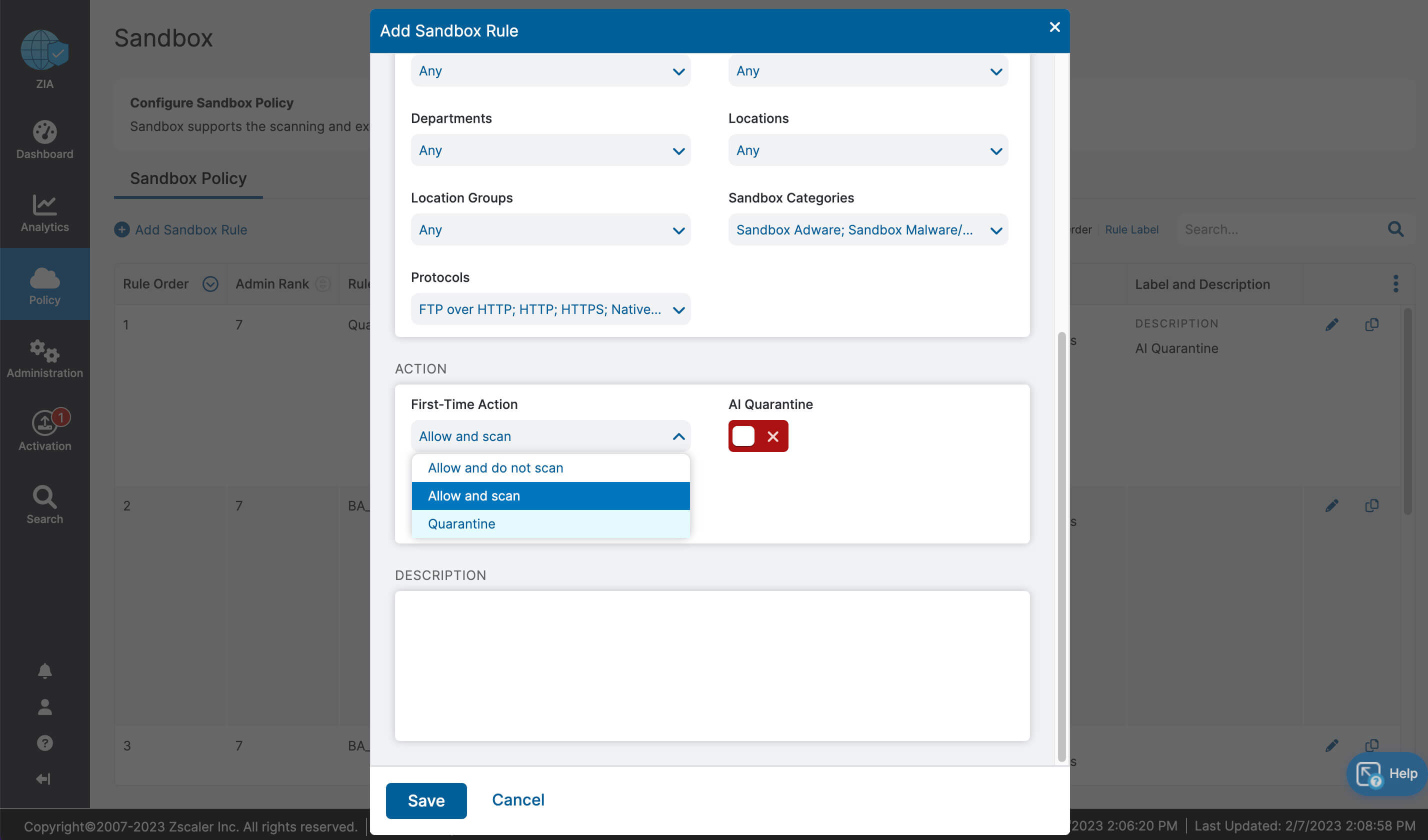
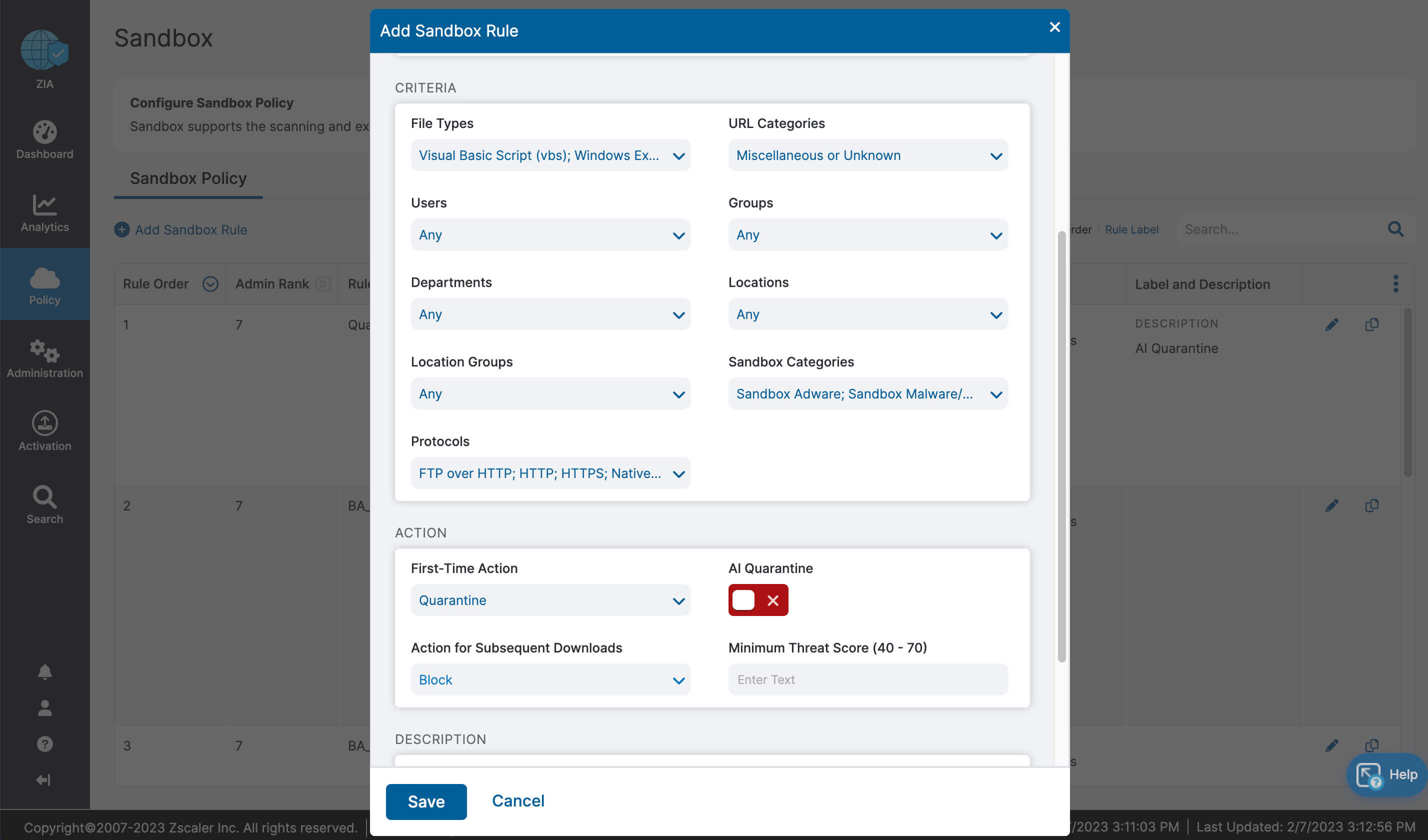
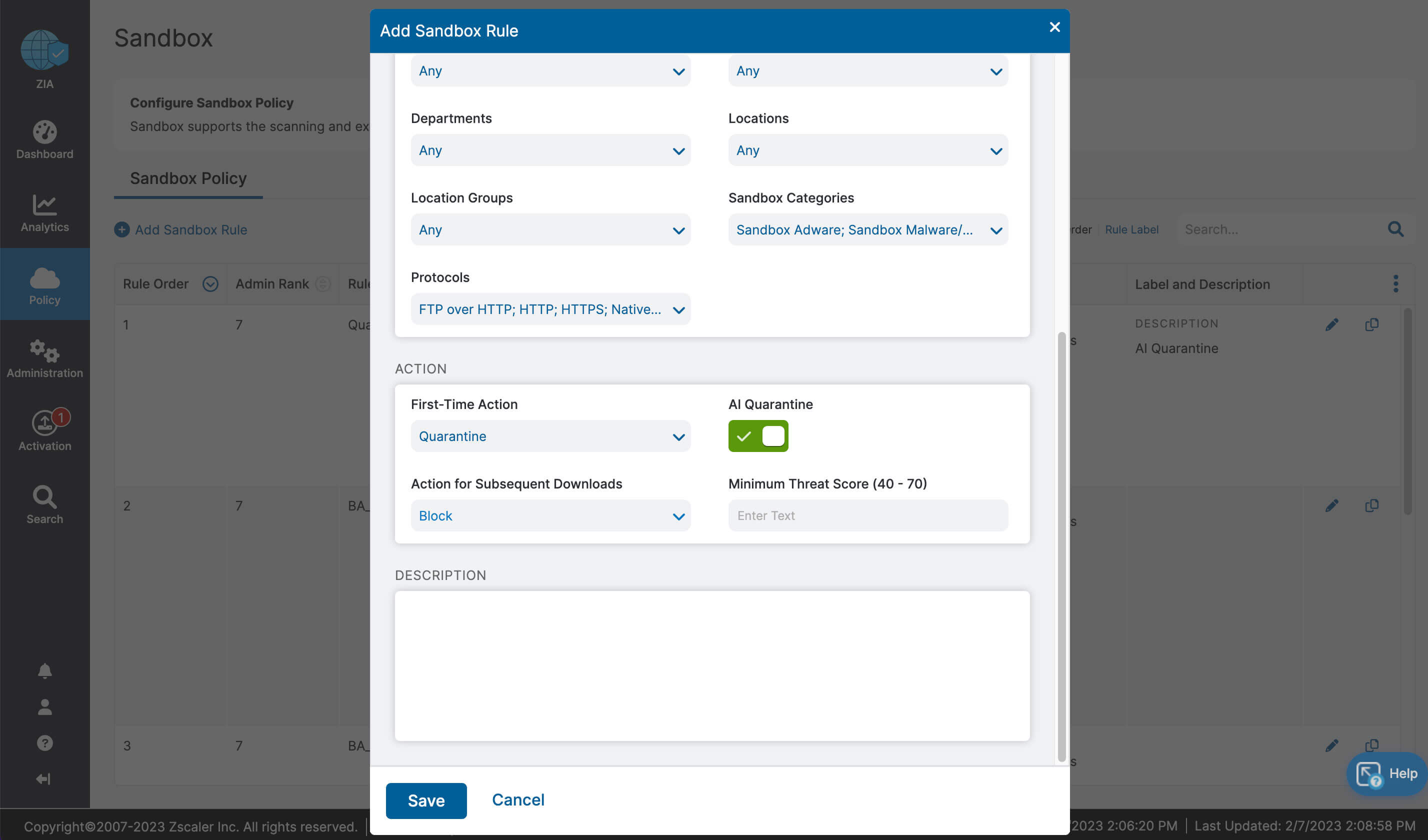
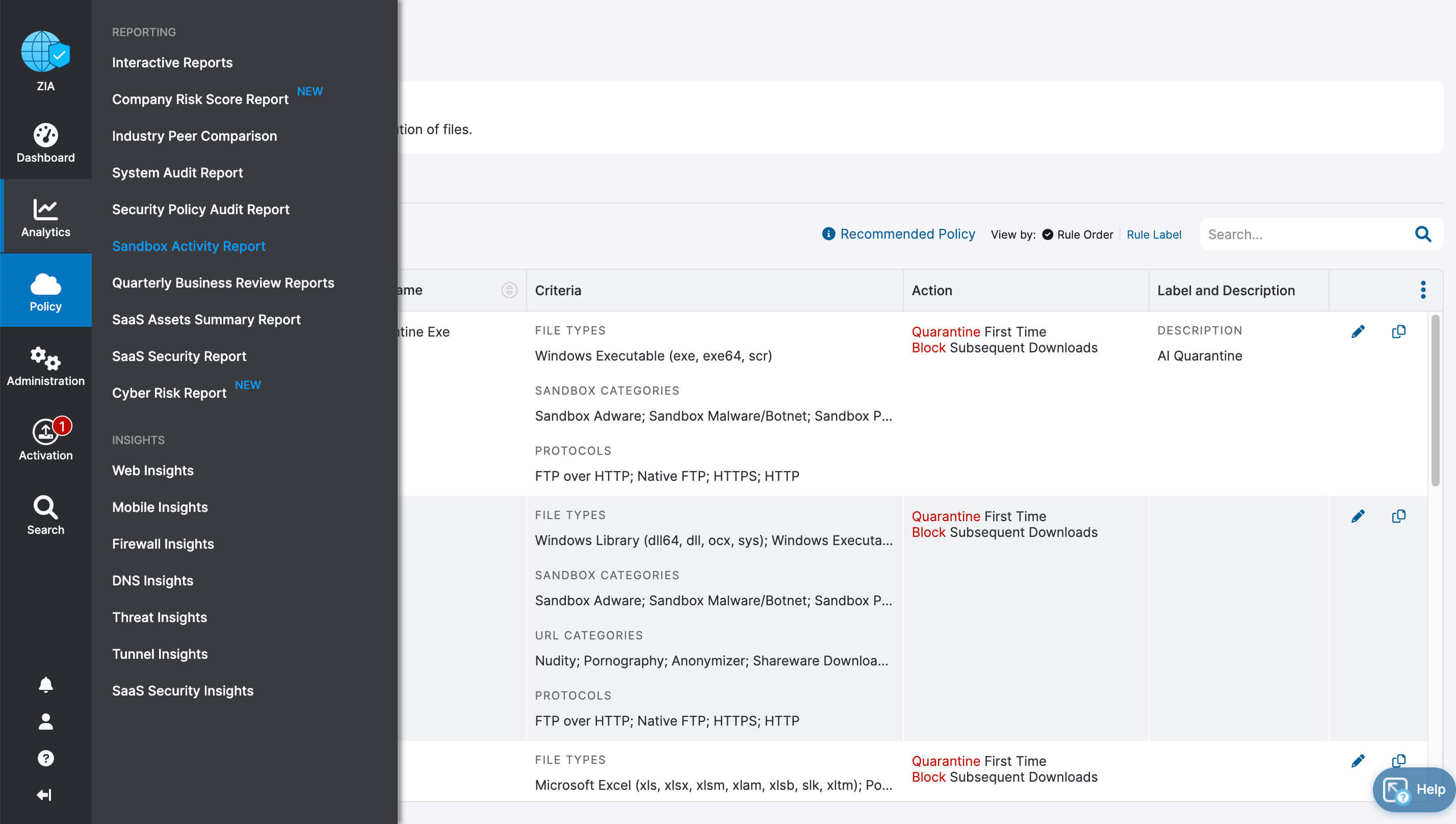
Let’s recap what we learned about ZIA for Microsoft 365:
- Fast, secure and reliable access to Microsoft 365
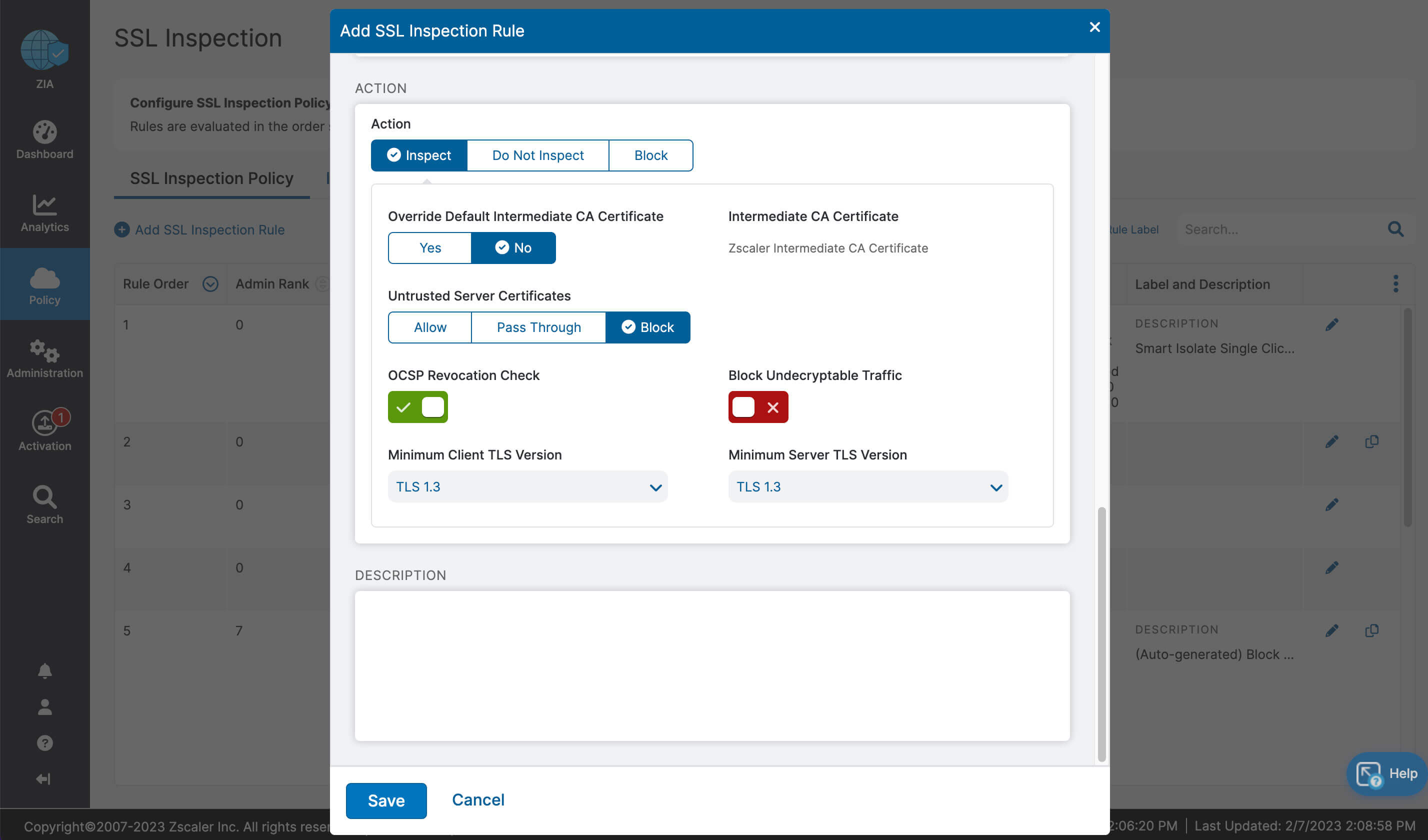
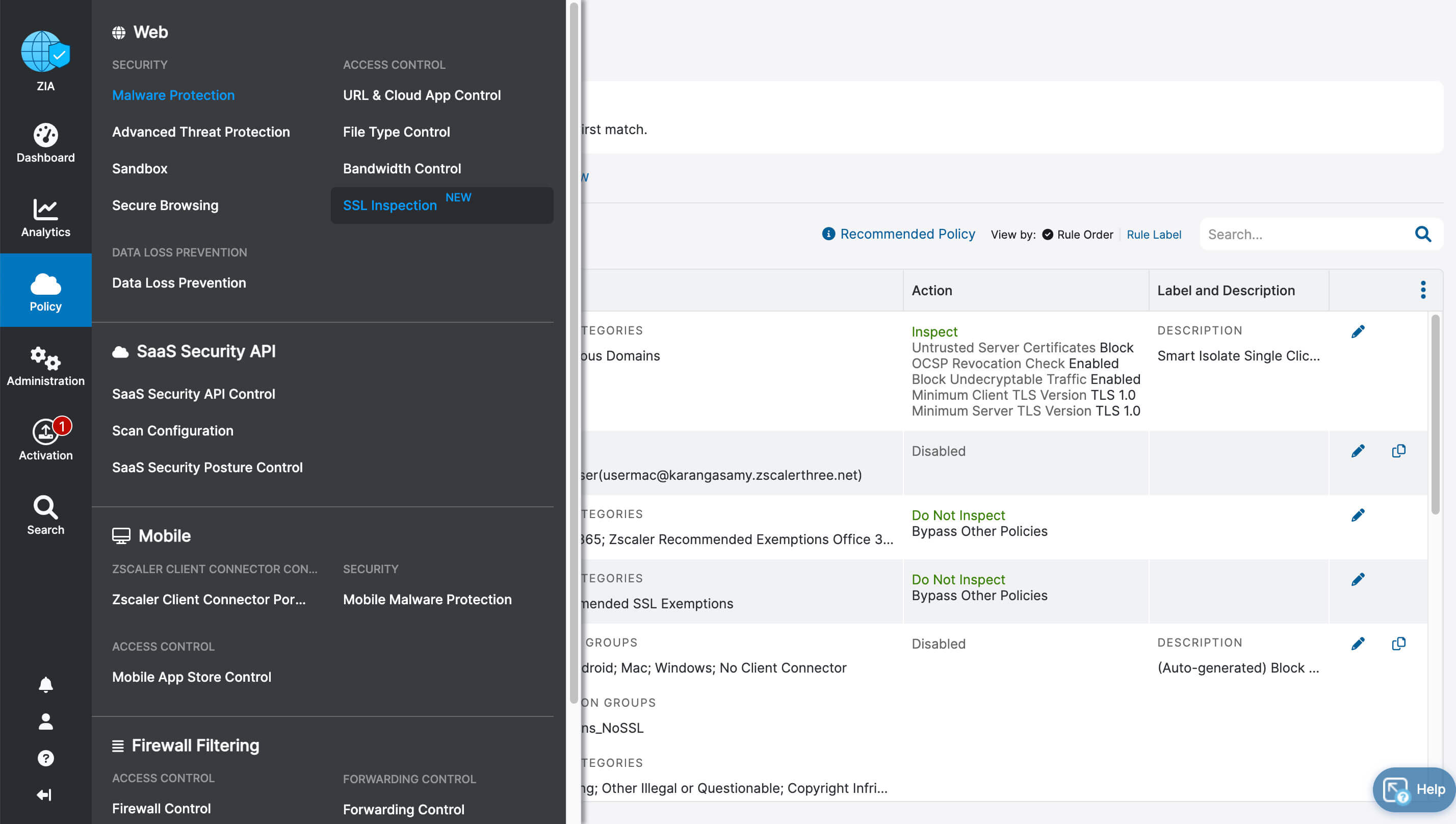
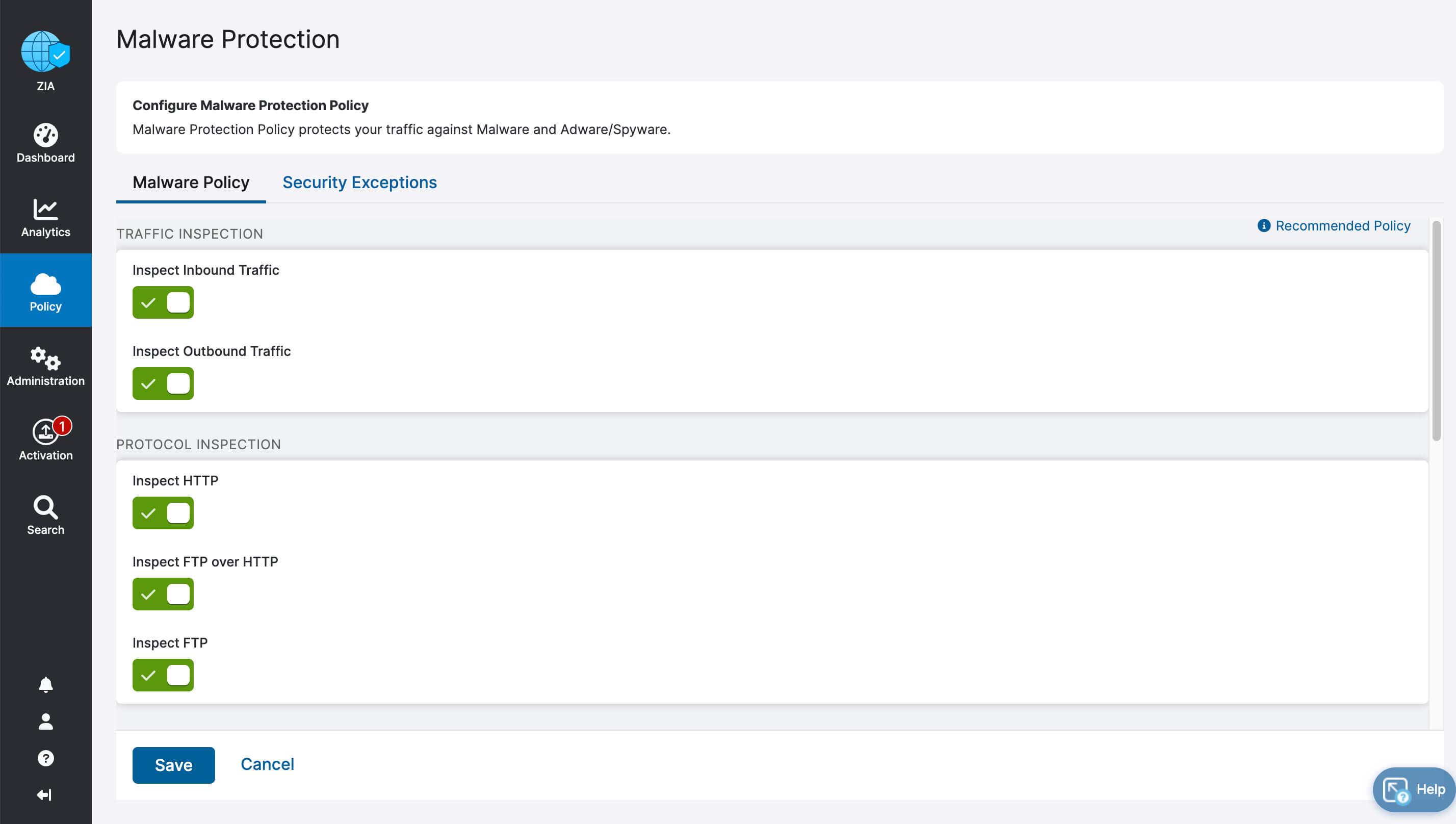
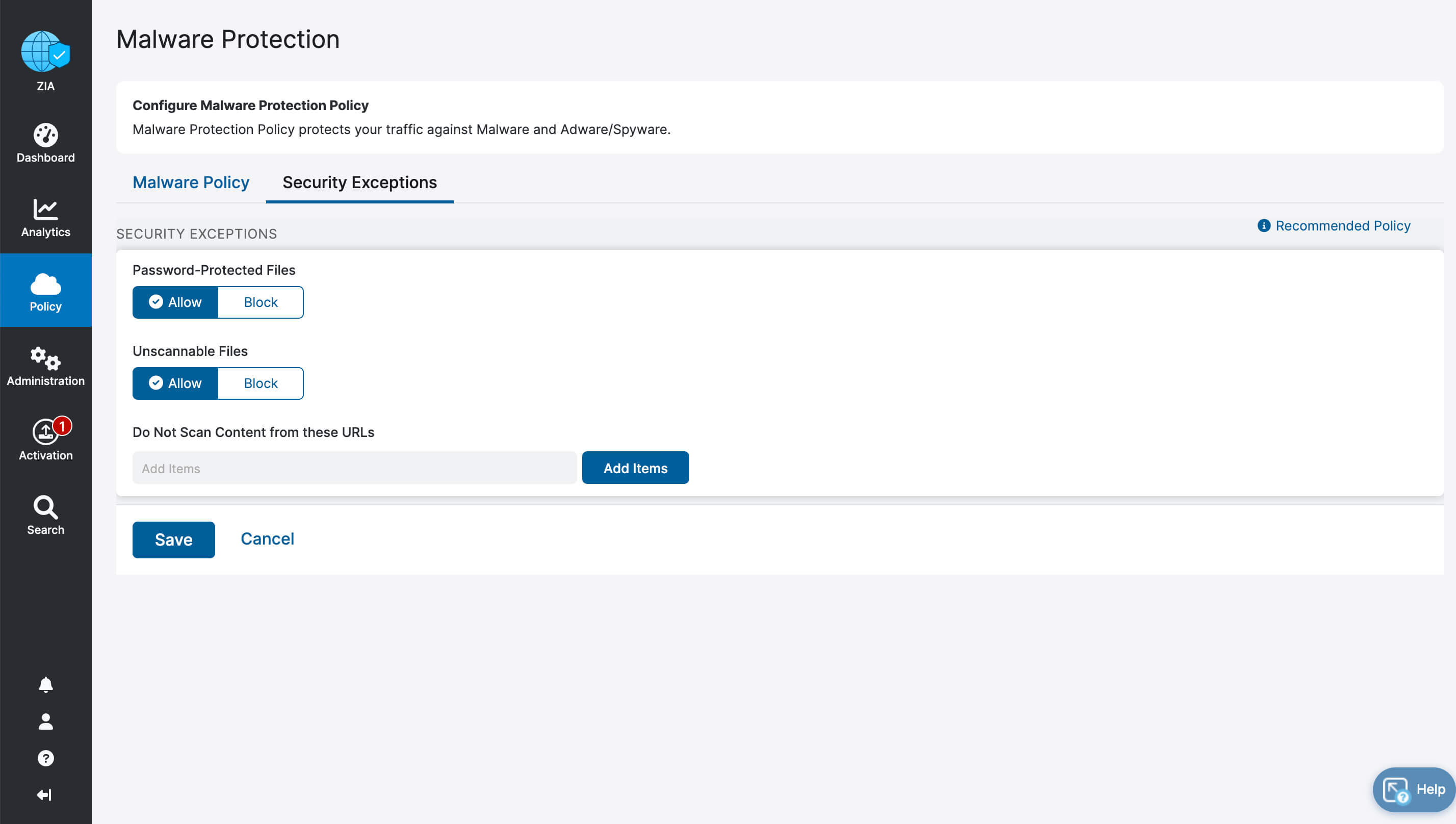
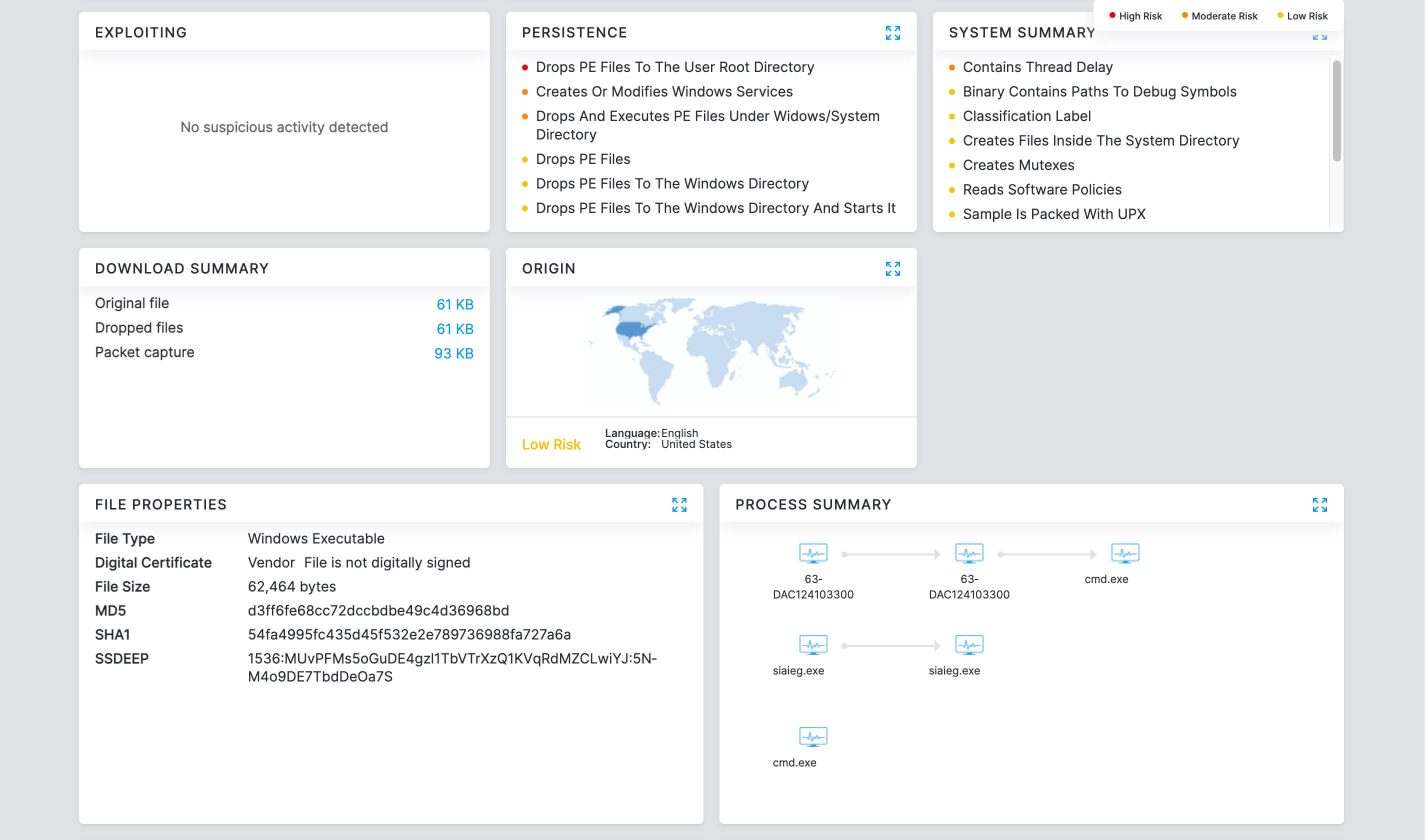
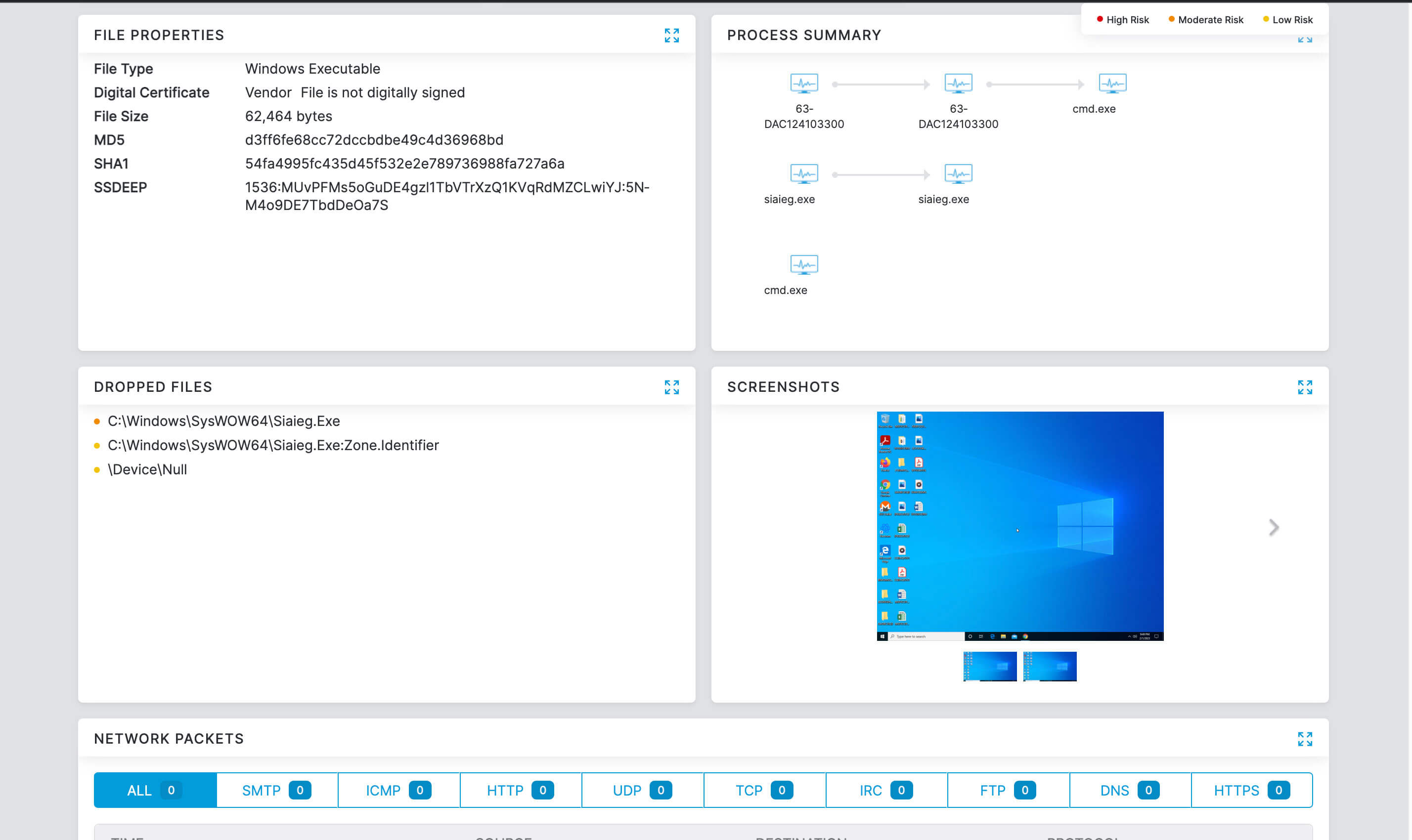
- Complete inspection of all traffic with innovative in-line prevention, detection and data loss protection built in
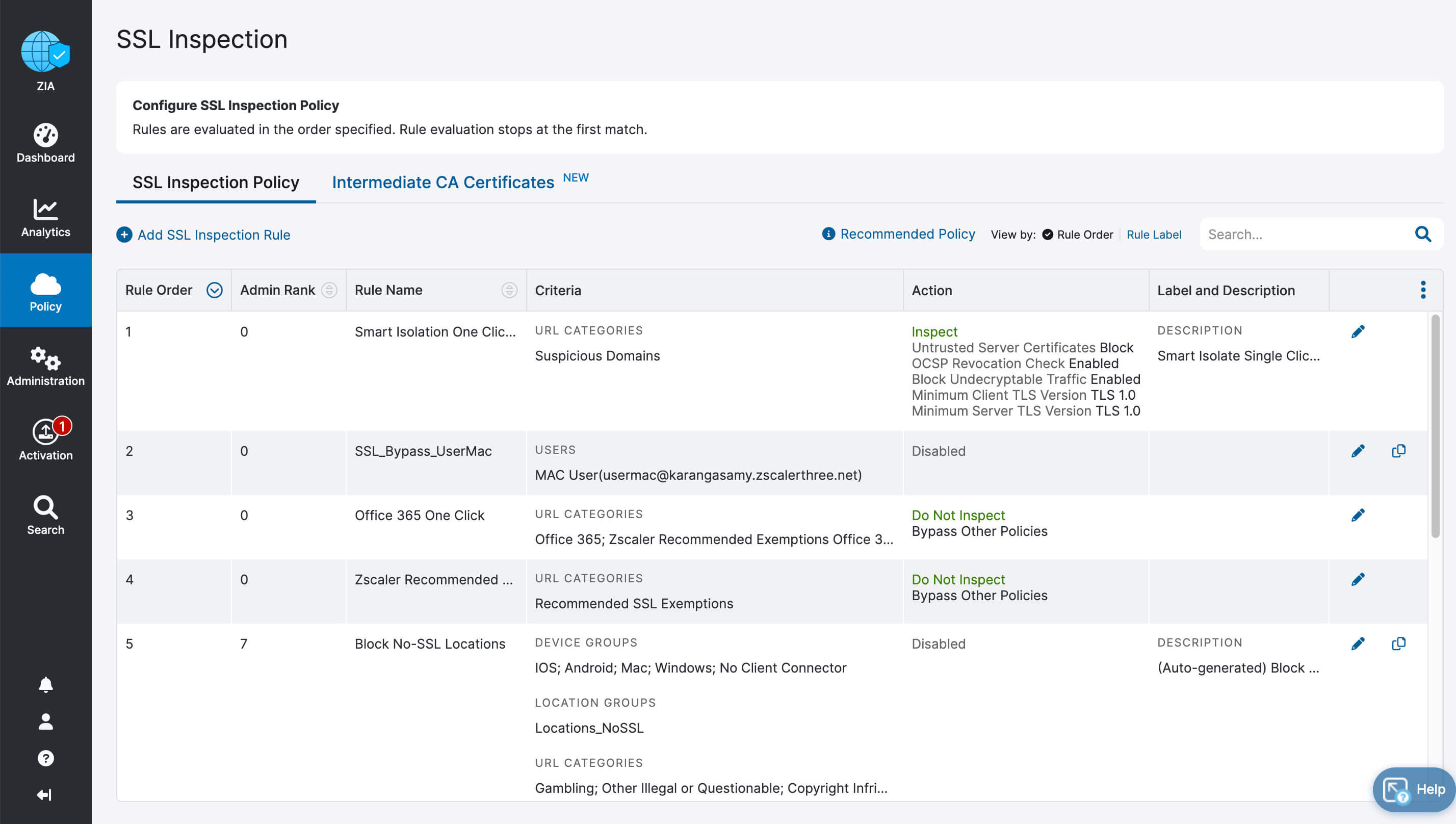
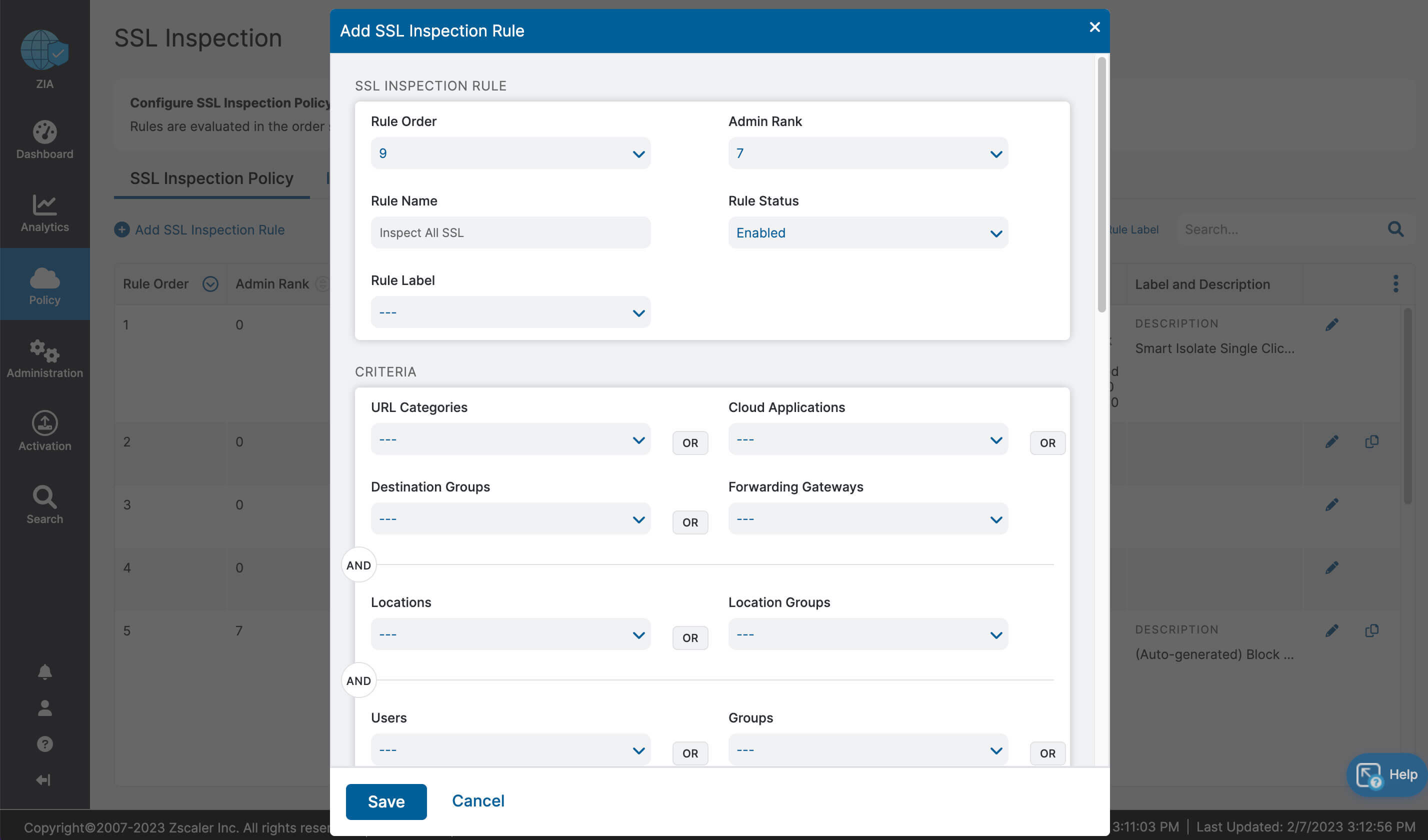
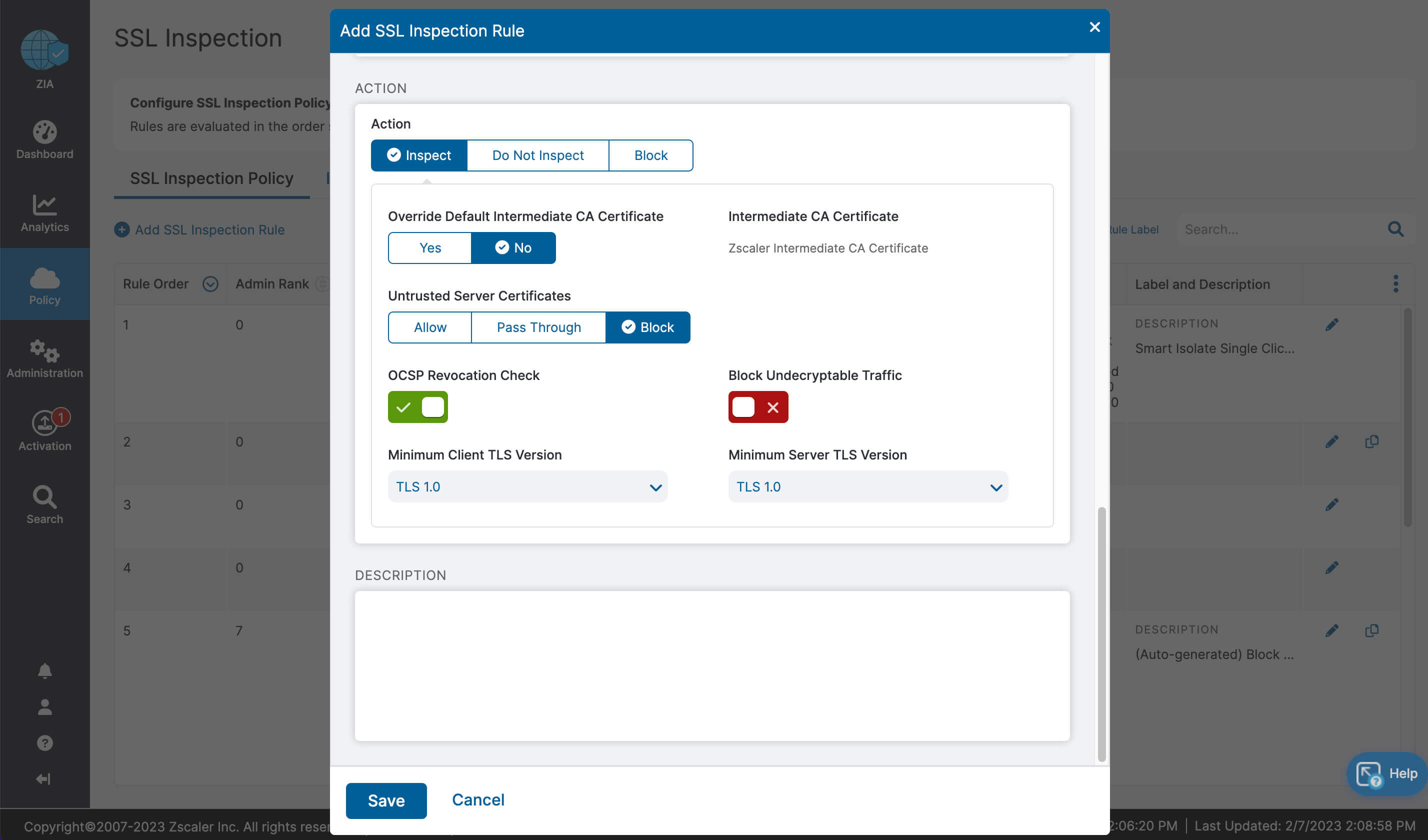
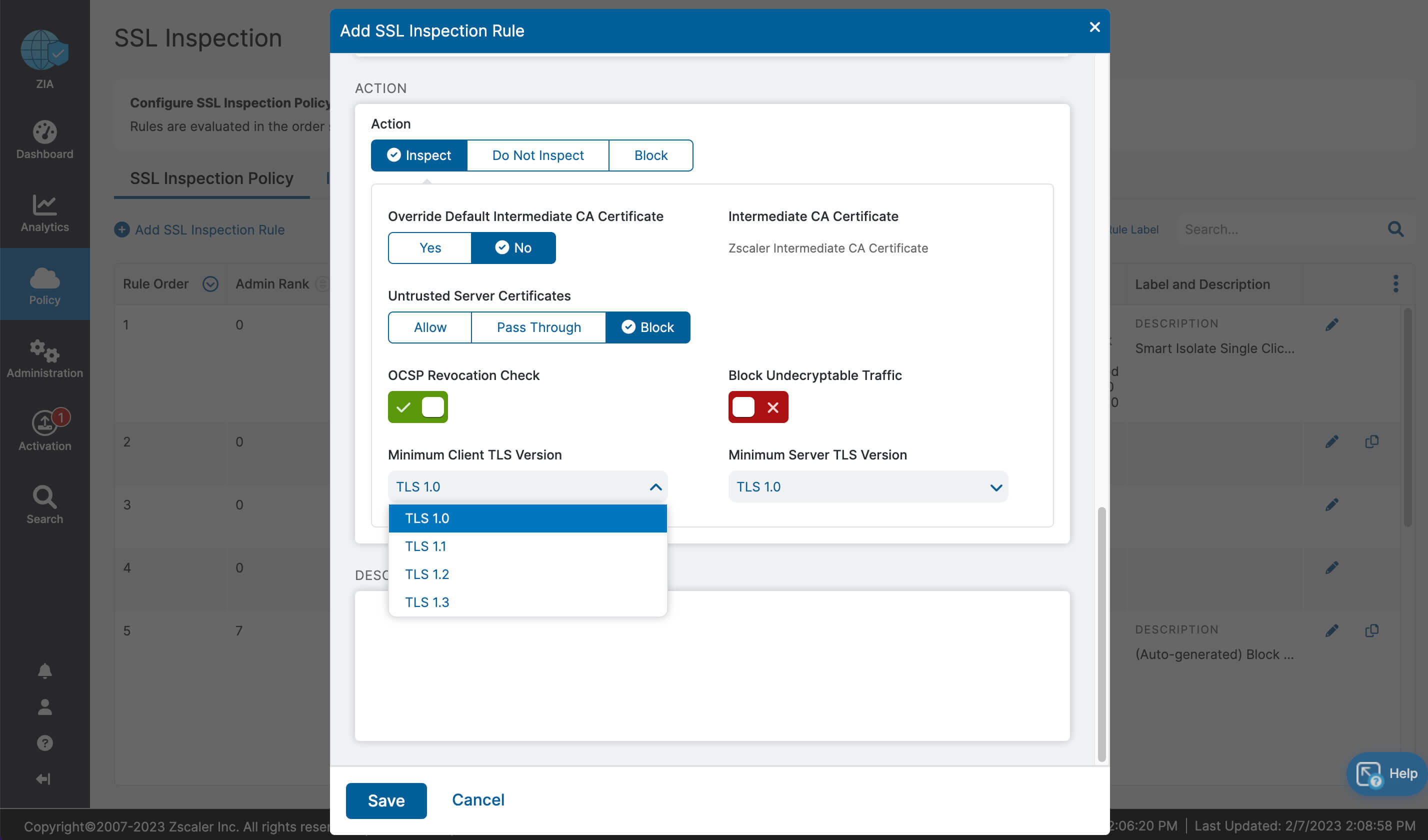
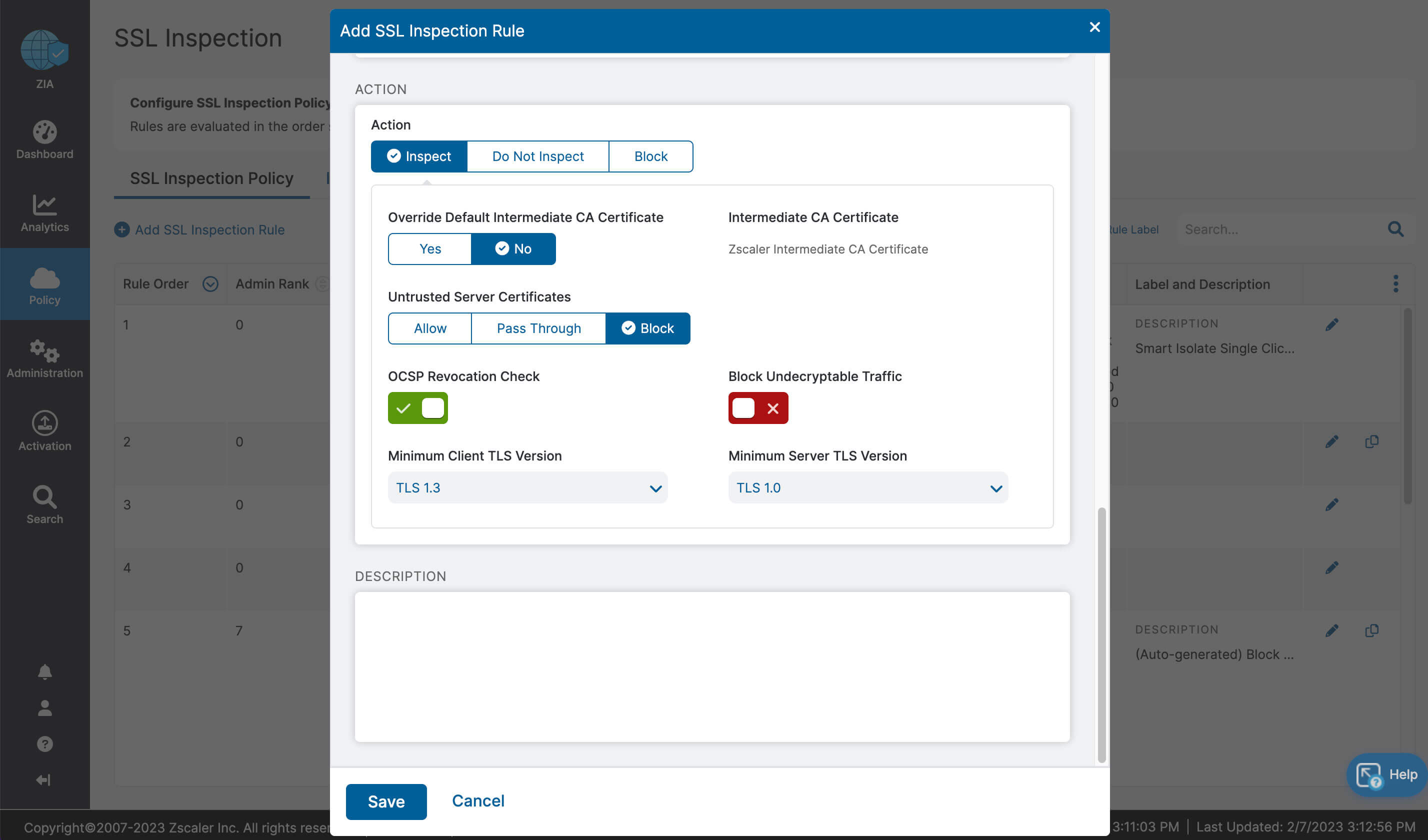
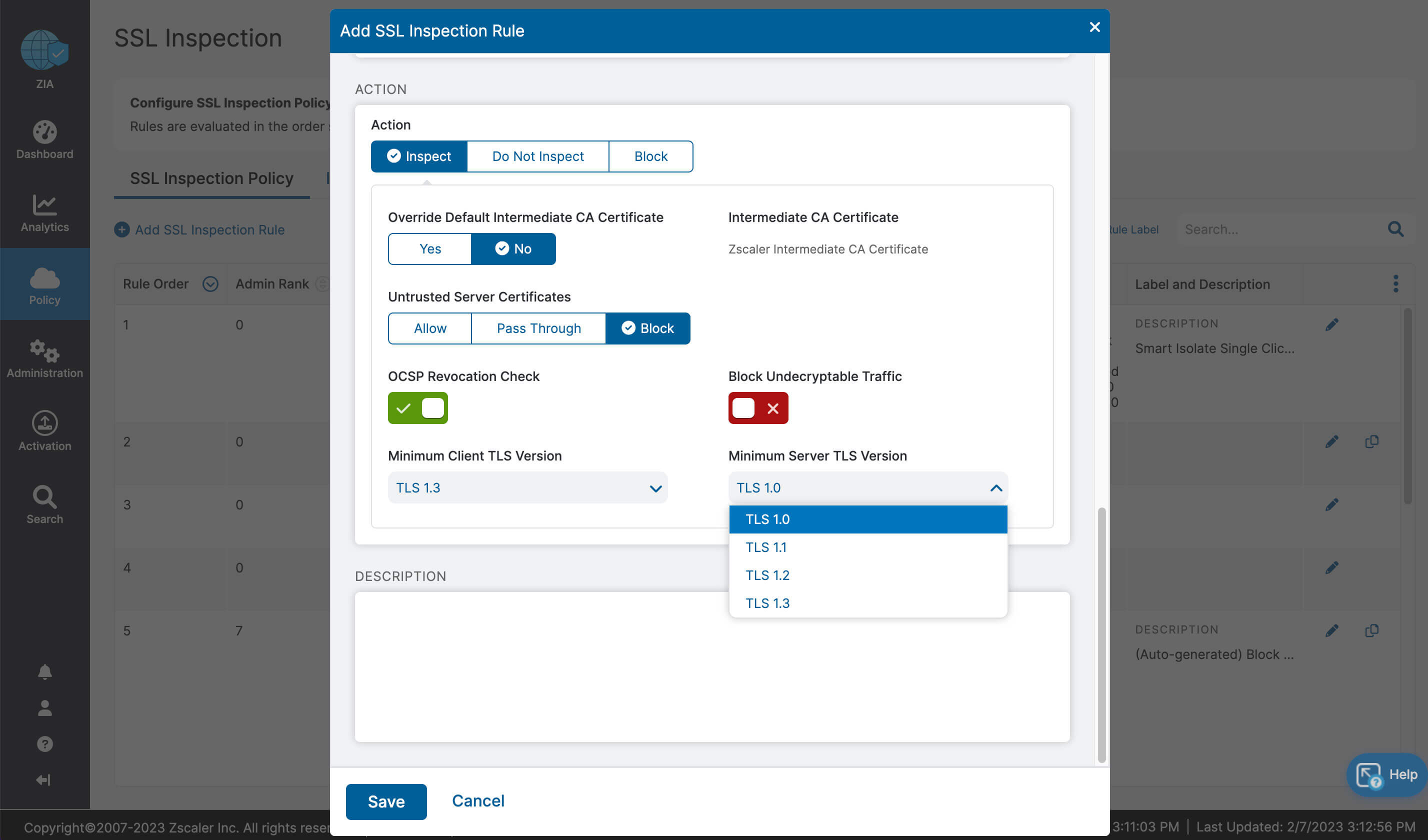
- Drastically simplified management with one-click configuration
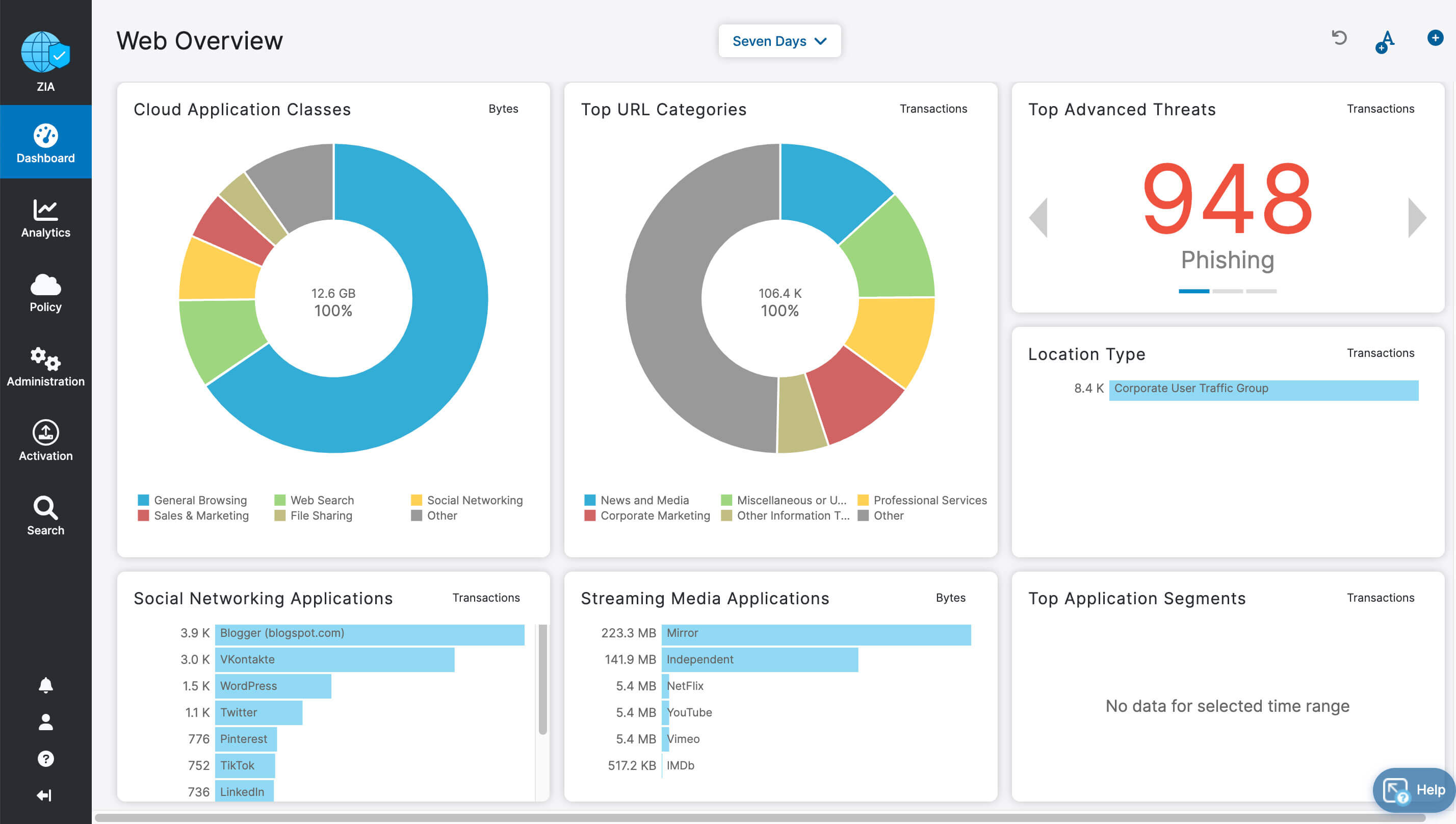
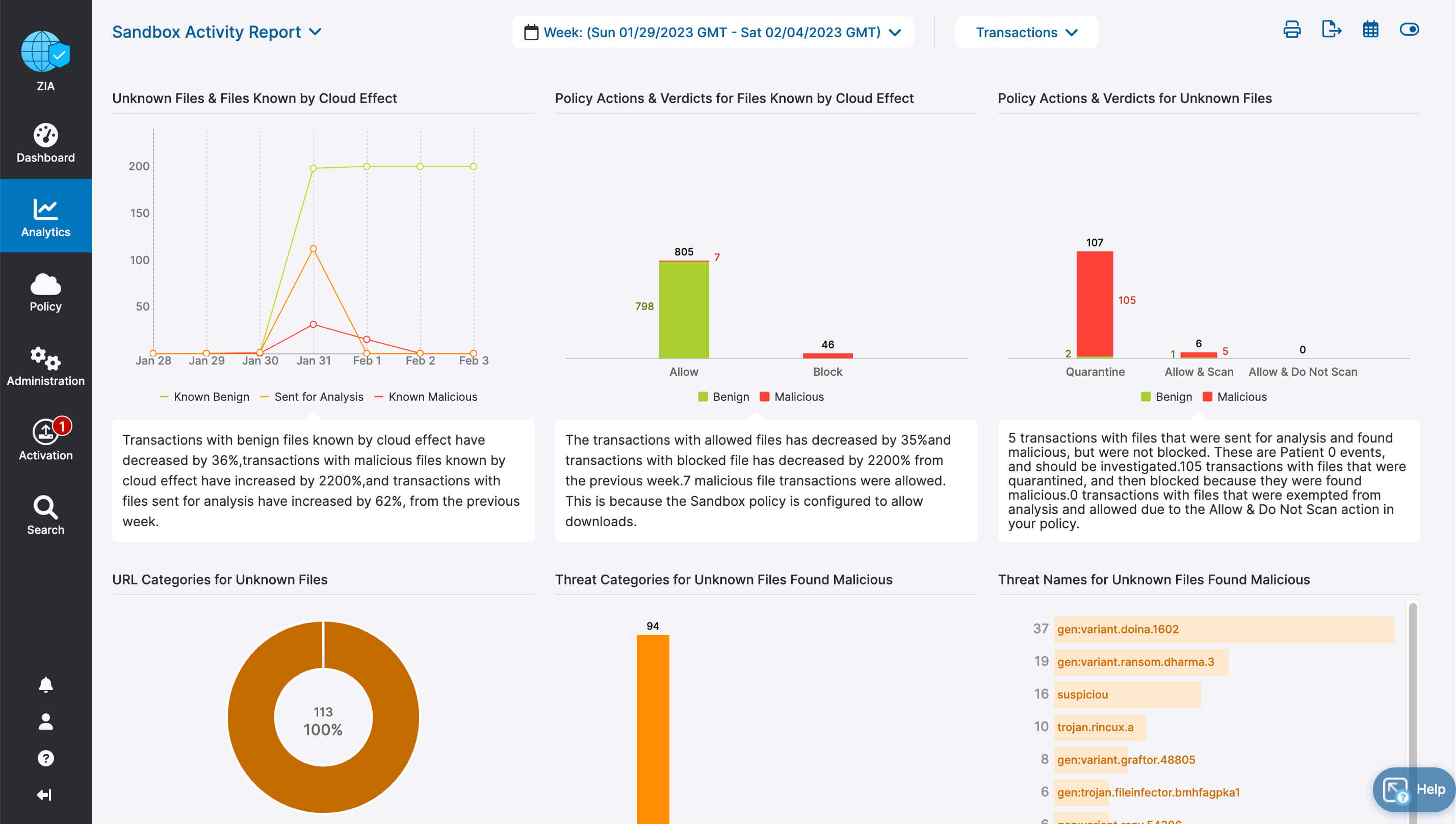
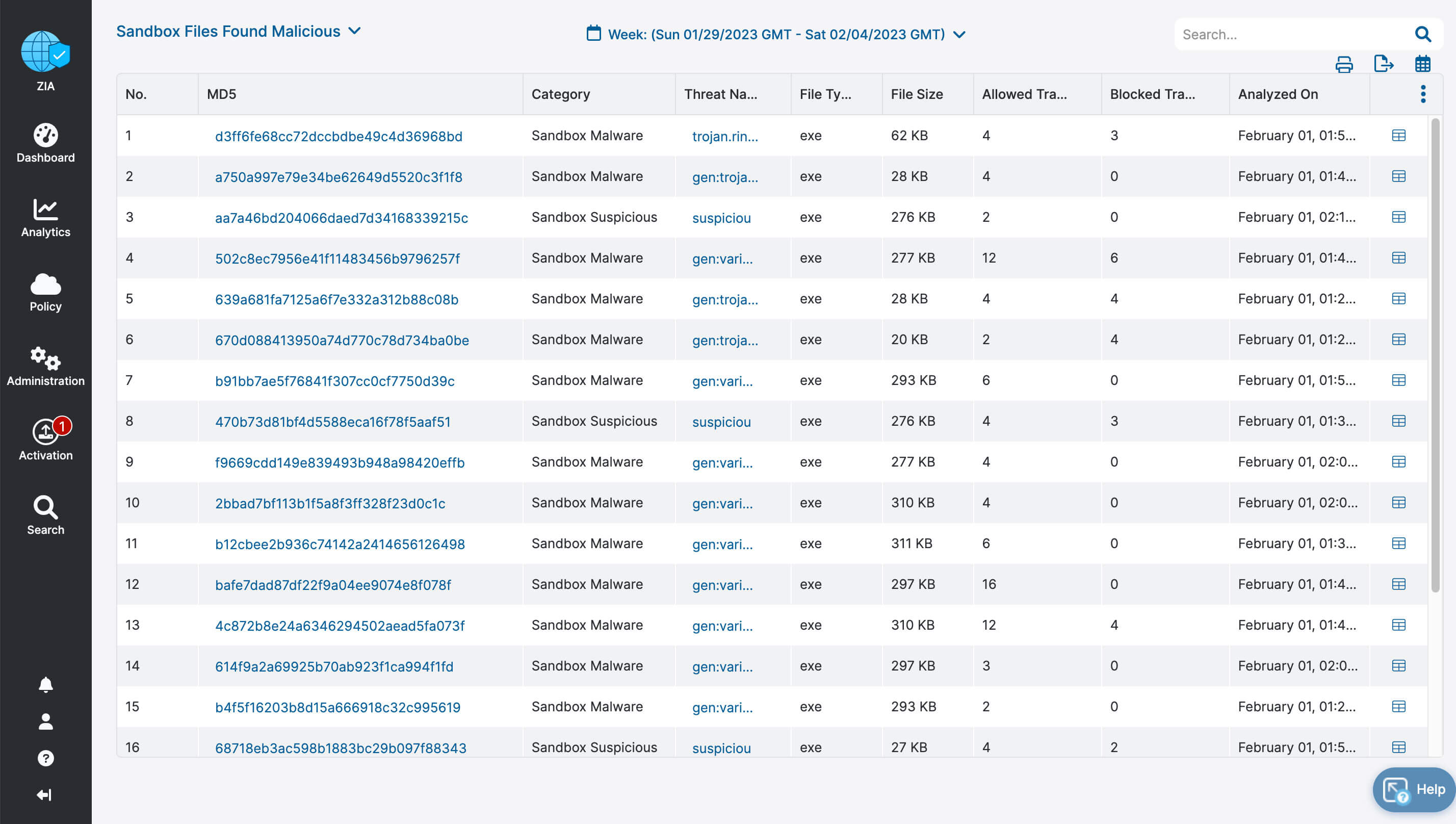
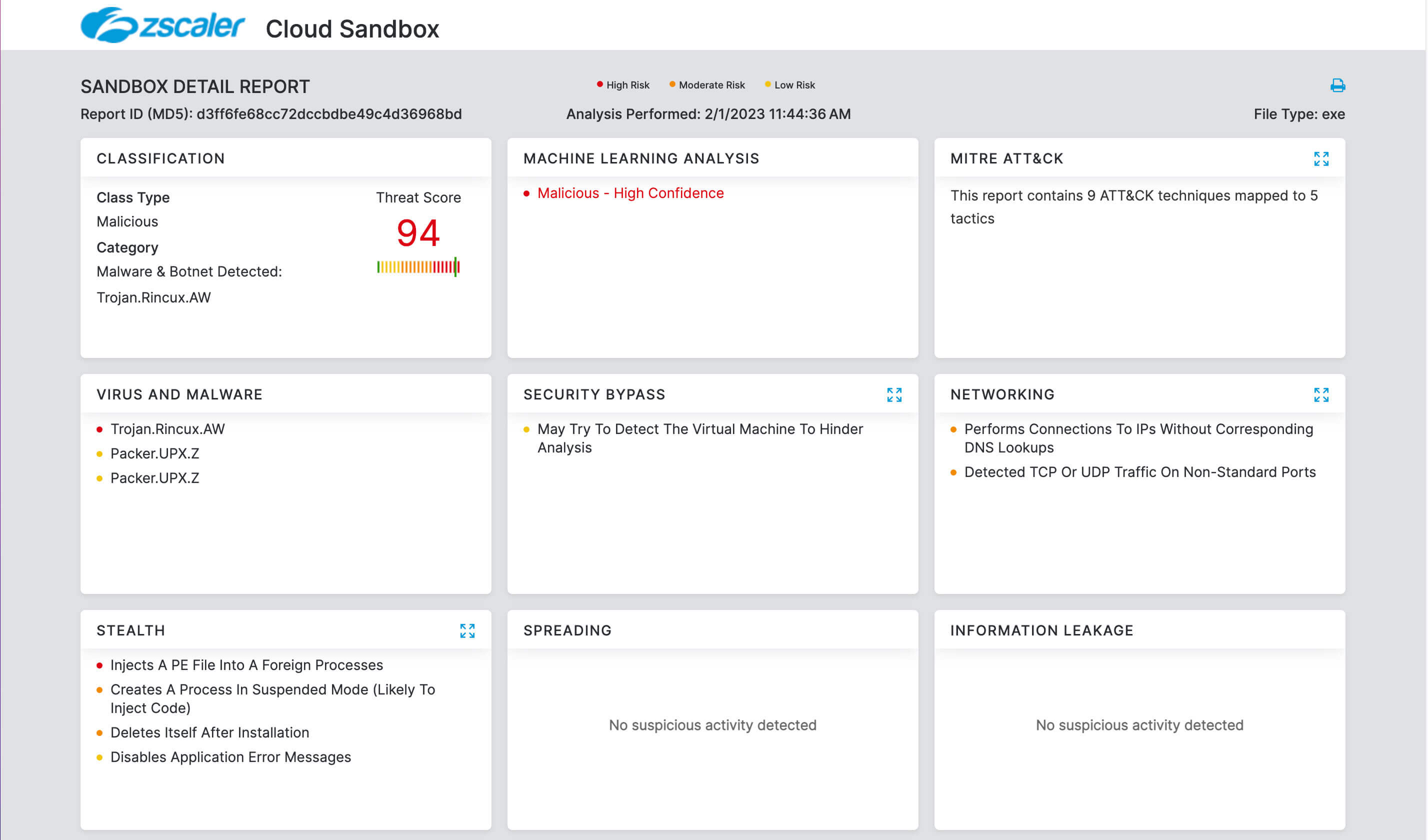
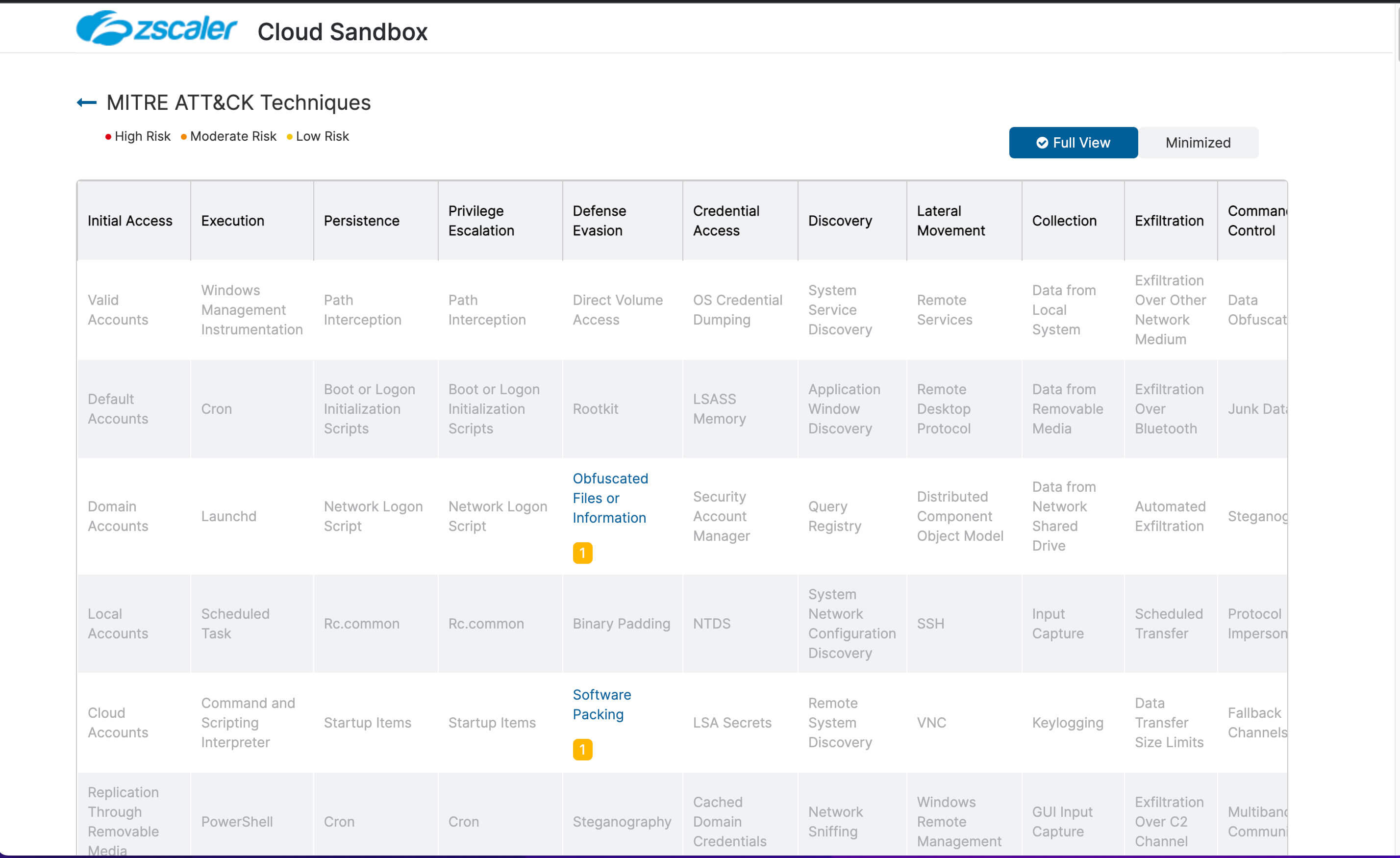
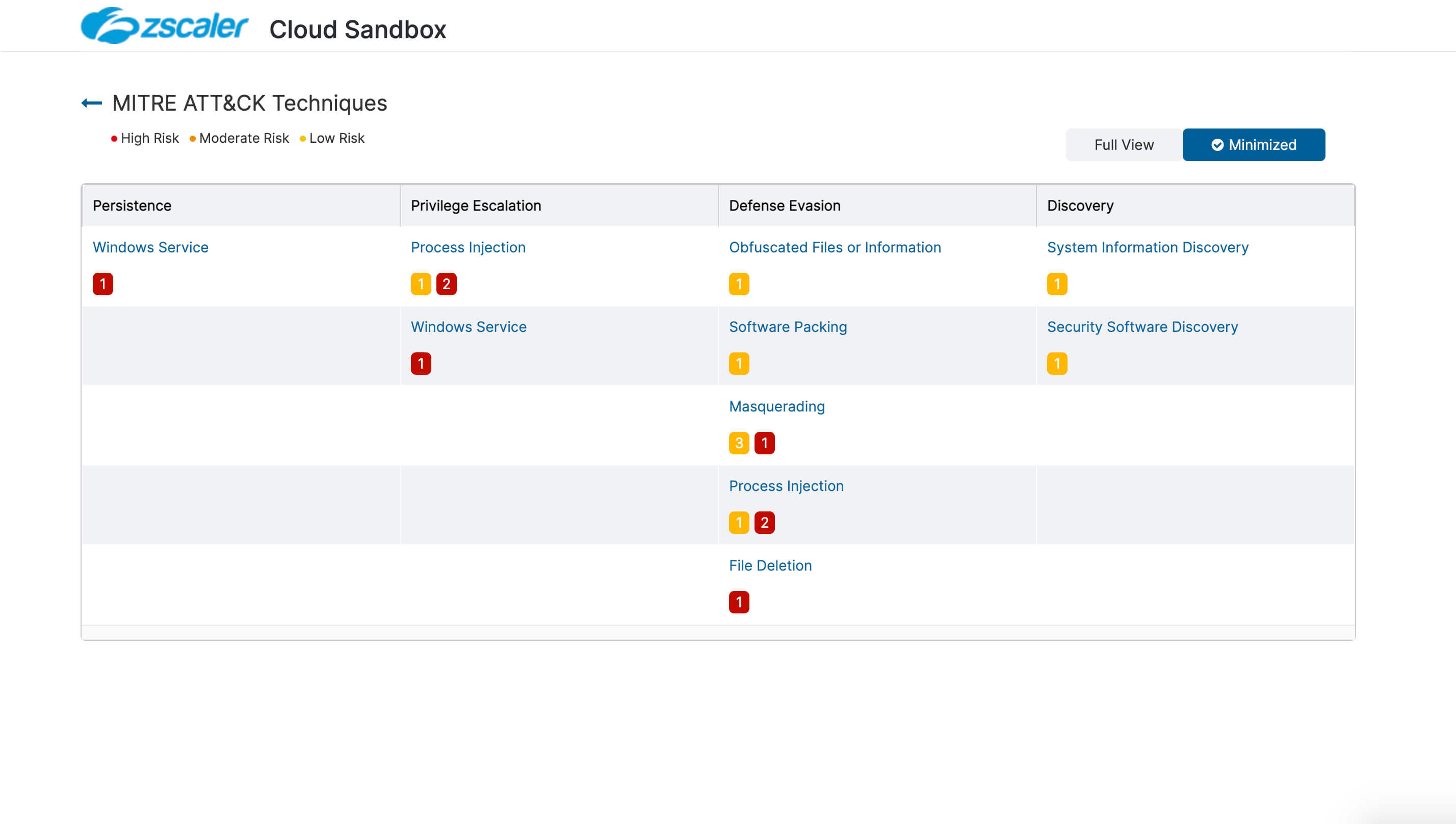
- Deep insights for users, apps, locations, traffic flows, and more